Top 300 Best Security Providers, Resources, Services
A
B
C
D
E
F
G
H
I
J
K
L
M
N
O
P
Q
R
S
T
U
V
W
X
Y
Z
- A -
- 3 iPhone security settings to lock down before it's too late - "Apple's Face ID is a good start, but you need to take your iPhone security further."
- 3 words that can save your life - "What3words: The app that can save your life. Police have urged everyone to download a smartphone app they say has already saved several lives. What is it and how does it work?"
- 3-2-1 Backup Rule Sucks - "As in most things associated with technology, what at one time is 'timeless' is at the next moment relegated to the scrap heap of history. Or perhaps to be more kind, it’s time for version 2 of the 3-2-1 backup strategy. While it doesn’t roll off the tongue as easily as the 3-2-1 backup strategy,there are multiple strategies ranging from 3-1-2 to 3-2-2 and even a 3-2-3 backup configurations that need to be considered by modern agile businesses."
- 4GB SPY VIDEO CAMERA WATCH W / HIDDEN CAMERA V2 - from BUDGETGADGETS.COM.
- 4 ways to avoid being a victim of Russian cyberwarfare - "Follow these four simple steps to outflank Putin’s digital foot soldiers."
- 5 Best VPN apps for Apple TV - "Setting up a VPN on your Apple TV 4K allows you to avoid geographic region restrictions and access services not normally available to you. With tvOS 17, VPN apps can now be installed on the Apple TV directly."
- 6 Best Indoor Security Cameras 2021 - "Cameras can offer peace of mind, but choose carefully when you’re inviting one into your home."
- 7 benefits of using a VPN (spoiler: it could save you money) - "We all regularly use the internet nowadays for a variety of different purposes. Whether it’s to keep in touch with friends and family, to work from home, or to conduct our banking and bill paying online, it’s important to be secure. One of the best ways to keep yourself secure and your activity private is to use a VPN."
- 7 new security features Apple quietly announced at WWDC 2021 - "While a two-hour (!) Keynote, usually filled with emoji, speaks out about security, the company also quietly introduces some new security and privacy-focused features at the WWDC developer session. did. Here are some of the most interesting and important ones."
- 7 Tricks to Spot Hidden Cameras in Your Next Airbnb - "Cams really may hide in Airbnb bedrooms, but there are cheap and effective ways to sniff them out: 1. Check out the local Wi-Fi network. Most Airbnbs offer some kind of guest Wi-Fi. 2. Bring up your Bluetooth. If cameras aren't connected to Wi-Fi, you can still pick them up with your Bluetooth. 3. Do a pass with a flashlight. 4. Scan for infrared eyes. 5. Use a camera-spotting app. 6. Inspect the vents. 7. Bring out an infrared scanner."
- 8GB DIGITAL SPY PEN - image capture, video recording (VOX).
- 10-Day Crash Course on Surviving the Apocalypse - "I wanted to learn how to prepare for disaster. It turned out I needed skills, yes — but the first thing was learning how to breathe."
- 10 Personal Safety Devices That Will Make Every Hotel Room Feel Secure - "From portable door stop alarms to carbon monoxide detectors, the 10 devices every solo traveler needs."
- 12 Best Browsers for Privacy & Security in 2020 - MacTribe.
- 12 Countries Where You Can Buy Citizenship (and a second Passport) - "After the 2016 presidential election, so many people were dreaming about moving out of the US that Canada’s immigration website crashed. Now, the idea of becoming an expat is getting hot again. According to a recent YouGov survey, 31% of Americans say they are interested in bolting if their candidate isn’t elected in the upcoming November elections. Tom Hanks and Rita Wilson made headlines when they recently became honorary Greek citizens and received passports."
- 14 best TSA-approved locks for trusted luggage security - "It makes sense that travelers want to protect their valuables while sending their gear into the unknowns of the airport, but it’s equally important for the TSA to be able to inspect checked luggage if and when the need arises. That’s where TSA-approved and recognized locks come into play. These specially-made locks were designed to secure luggage and valuables but also allow the TSA to open your baggage when necessary."
- 19 alarming cybercrime statistics for 2019 - BroadbandSearch.
- 29 Changes In Clothing Fashion That Made Stealing Easier Or Harder - "As Shared By Former Pickpockets And Magicians Online."
- 314 Things the Government Might Know About You - "Two reporters spent over a month compiling and analyzing information about the reams of data the U.S. government collects about Americans."
- A Face Search Engine Anyone Can Use Is Alarmingly Accurate - "PimEyes is a paid service that finds photos of a person from across the internet, including some the person may not want exposed. 'We’re just a tool provider,' its owner said."
- A Hacker Found a Way to Take Over Any Apple Webcam - "The Safari vulnerabilities have been patched, but they would have given an alarming amount of access."
- A-list must-have? An £80,000 protection dog. Called Kevin - "Foreign royalty, billionaires and celebrities are replacing their private security with four-legged bodyguards that are also devoted family pets. Hilary Rose on the rise of the furry status symbol."
- A woman got tired of her mail getting stolen. She sent herself an Apple AirTag to help catch the thieves - "Authorities in Los Alamos arrested two suspects on Monday with the help of an Apple AirTag locator device the woman had mailed to herself, the sheriff’s office said in a news release."
 - Addalock Portable Door Lock - since 2021. "The Original Portable Door Lock, Travel Lock, AirBNB Lock, School Lockdown Lock." The Addalock is a portable door lock that can be easily installed and removed in seconds on almost any hinged door that opens inwards giving you added privacy once you are locked behind it. Addalock can be installed on the front door or any other doors of your home where you require that additional privacy. The Addalock is an ideal travel lock that you can use on your hotel/motel or rental unit and ideal for students away at college. The Addalock is made from chrome plated carbon steel and together with its unique shape makes it adjustable to almost any door thickness. Each Addalock comes with a travel pouch. The Addalock became TikTok famous last year as an easy-to-use and inexpensive gadget for travel safety, especially for solo female travelers. For $17.95 a pop, it's a no-brainer.
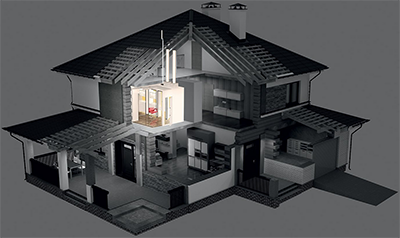 - Agresti Strong & panic room - "A custom made space inside your home, protected by chromium-carbide steel walls and door, certified up to Grade 5. Elegant furniture for storing jewelry and watches, last generation technological equipment to guarantee your security in the event of theft or burglary."
- Air fryers among ‘smart device spies’ trying to record you - "Are you under surveillance in your own home? Research by Which? suggests that smart TVs, watches and speakers could be sending your data to China."
- AirTags are being used to steal cars - "Apple still has a lot of work to do with safety and privacy here. According to a new report released by the York Regional Police, car thieves are using AirTags to mark, track, and steal vehicles."
- AK-47 | Avtomat Kalashnikova - is a selective fire, gas operated 7.62mm assault rifle. The original AK-47 and its numerous variants are the most widely used and popular assault rifles in the world. KALISHNIKOV HOMEPAGE - dedicated to Kalashnikov and his firearms.
- All the Data Apple Collects About You & How to Limit It - "Cupertino puts privacy first in a lot of its products. But the company still gathers a bunch of your information."
- Amazon's Dark Secret: It Has Failed to Protect Your Data - "Voyeurs. Sabotaged accounts. Backdoor schemes. For years, the retail giant has handled your information less carefully than it handles your packages."
- An Essential Guide on How to Keep Yourself Private Online in 2019 - "Online Privacy has become a major concern for every security agency and the citizens ever since the big data leak has taken place. Here is a Comprehensive Guide to Online Privacy 2019 that you must follow to stop your data being leaked to different hackers. To make this easy for you to understand we have divided this guide into three following sections."
- An Open Source Effort to Encrypt the Internet of Things - "IoT is a security hellscape. One cryptography company has a plan to make it a little bit less so."
- Anti-surveillance gadgets for protesters - Ars Technica.
- Anyone can use this powerful facial-recognition tool - and that's a problem - "If you upload a picture of your face to PimEyes' website, it will immediately show you any pictures of yourself that the company has found around the internet. You might recognize all of them, or be surprised (or, perhaps, even horrified) by some; these images may include anything from wedding or vacation snapshots to pornographic images."
- App Knows If Your iPhone Has Been Hacked - Do You? - "How do you know if your iPhone has been hacked? There's an app for that. There are no iPhone anti-virus apps in the App Store."
- APP THAT ENCRYPTS YOUR PHOTOS FROM CAMERA TO CLOUD - Wired.
 - Apple AirTag - since 2021. "Personalize your AirTag with free engraving. Only at Apple." AirTag is an easy way to keep track of your stuff. Attach one to your keys, slip another one in your backpack. And just like that, they’re on your radar in the Find My app. AirTag has your back.
- Apple AirTags - 'A perfect tool for stalking' - "The button-sized devices are designed to work with Apple's 'Find My' network to locate lost items. But there have been multiple reports in the US of the devices being used to track people."
- Apple, Google, Amazon & Facebook are always listening unless you change these settings - "If you want to take control of your privacy, here’s how to stop your smart devices from listening."
- Apple Issues New Spyware Attack Warning To iPhone Users - "Apple has issued a new spyware attack warning to users in 98 countries. It's the second time the iPhone maker has released an alert of this nature over the last few months. Apple issued a similar spyware alert back in April when it warned iPhone users in 92 countries they had been targeted in attacks."
- Apple Watch: How To Check If Your Apple Watch Is Infected With Spyware - "When your watch is a sophisticated computing device, it’s also a target for hackers. Now you can scan your Apple Watch for spyware; here’s how."
- Apple’s Stunning New iPhone Feature Is A Triumphant Success - "Apple’s recently-launched iPhone privacy feature, App Tracking Transparency (ATT) is proving to be a triumphant success - that is, if you care about privacy."
 - Arlo Pro Security System with Siren - 3 Rechargeable Wire-Free HD Cameras with Audio, Indoor/Outdoor, Night Vision (VMS4330). "The world's first 100 percent wireless high-definition smart home security camera."
 - Armatix - 'Smart' Firearms.
- ARMOR GROUP - the world's leading security solutions group.
- ARMORCO - "Your protection is our priority." Distributor / manufacturer of hi-tech bullet resistant materials and personal protection products.
- ARMY TECHNOLOGY - the website for the defence industries - army.
- ‘Ask all the time: why do I need this?’ How to stop your vacuum from spying on you - "Even if you’re not gadget-obsessed, the odds are you’ve got at least one smart device at home. So how do you limit the internet of things from listening in?"
- ASSA ABLOY - the global leader in door opening solutions.
- Atlas VPN - "Fastest Free VPN Service." Atlas VPN is a free VPN app that ensures private browsing by changing your IP address and encrypting your connections.
- Atlas VPN Launches Its Free Mobile Service to Protect Security Online - "A new, reliable and free VPN will combat shady players for free VPN market share. All this, while keeping a strict no-logs policy and not pushing ads to its users."
- AUDI SECURITY CARS - "You are in an especially safe place when you’re in an Audi Security car".
 - AXON Flex - "A New Generation of Police Video Camera." The AXON Flex is a point-of-view video camera system designed to be worn by law enforcement officers to capture video and audio from their perspective. There also is an app that allows for the live viewing or immediate playback on a smart phone of what the camera captures. The unit is activated simply by pressing the large button on the power pack, which is attached to the camera via a small wire.
A
B
C
D
E
F
G
H
I
J
K
L
M
N
O
P
Q
R
S
T
U
V
W
X
Y
Z
- B -
- BAE SYSTEMS - global company engaged in the development, delivery and support of advanced defence, security and aerospace systems in the air.
- BALLISTIC STANDARDS - independent product verification and qualification testing.
- Barracuda Web Application Firewall - since 2003. "As one of the lines of defense against automated bots, the Barracuda Web Application Firewall can issue a challenge in the form of CAPTCHA tests."
- Beau Dietl & Associates - since 1985. New York private investigators specializing in background checks, asset recovery and security.
- Behind the One-Way Mirror: A Deep Dive Into the Technology of Corporate Surveillance - "Trackers are hiding in nearly every corner of today’s Internet, which is to say nearly every corner of modern life. The average web page shares data with dozens of third-parties. The average mobile app does the same, and many apps collect highly sensitive information like location and call records even when they’re not in use. Tracking also reaches into the physical world. Shopping centers use automatic license-plate readers to track traffic through their parking lots, then share that data with law enforcement."
- Belgian Malinois dog - U.S. Secret Service uses Belgian Malinois to guard the grounds of the White House.
- Best Outdoor Security Cameras - "These weatherproof devices can keep a watchful eye on your property and let you get on with life."
- best portable SSD - engadget.
- best VPNs for 2023 - "Don’t fall for the hyped-up, overly-marketed options."
- Beware the smart toaster: 18 tips for surviving the surveillance age - The Guardian.
- Billionaire bunkers: How the 1% are preparing for the apocalypse - "Say 'doomsday bunker' and most people would imagine a concrete room filled with cots and canned goods ..."
- Billionaires only, please! London vault for the ultra-rich opens - "Exclusive safety deposit bank near Harrods angles to be world’s most expensive."
- Billionaires' Survivalist Bunkers Go Absolutely Bonkers With Fiery Moats & Water Cannons - "Amid 'World War III' fears, apocalypse-fearing moguls are investing millions in survival strategies including rotating fireplaces out of 'Indiana Jones' and heightened tactical systems."
 - Blackphone 2 - "Privacy Without Compromise." The world’s first smartphone built from the ground up to be private by design. Secure voice, video, conferencing, file transfer, and text communications.
- BLACKWATER WORLDWIDE - a private military security company founded in 1997. Has now changed its name to Xe Services LLC.
 - Boing Black Smartphone - "Security, modularity and productivity delivered – all in one trusted mobile device." The Boeing Black has a dual-SIM capability that allows users to switch between government and commercial networks, and works globally on GSM, WCDMA, and LTE bands. Boeing said the smartphone's 5.2-inch-tall shell can be customized with additional sensors, an extra battery, satellite transceivers, biometrics, and other hardware.
- BOOK VAULT - two random hardcovers hollowed out to hold stuff.
- BOSCH - "Invented for life."
- BOTACH TACTICAL - "Your Professional Specialist Serving Those Protecting Our Great Country."
- Britain Has More Surveillance Cameras Per Person Than Any Country Except China. That's a Massive Risk to Our Free Society - "Facial recognition cameras are now creeping onto the streets of Britain and the U.S., yet most people aren't even aware."
- bunkers: Meet the man building bunkers for billionaires - "They are thousands of miles from conflict zones, but these home-owners are still prepping for Armageddon."
- bunkers: Why the super rich are building super luxury bunkers - "Operating theaters, bowling alleys and home cinemas: Not happy with safe rooms, the super-rich are building luxury fortresses."
A
B
C
D
E
F
G
H
I
J
K
L
M
N
O
P
Q
R
S
T
U
V
W
X
Y
Z
- C -
- CAMPCO - watches, law enforcement equipment, handcuffs, pepper spray, stun guns.
- Can The FBI Hack Into Private Signal Messages On A Locked iPhone? Evidence Indicates Yes - "Signal has become the de facto king of secure messaging apps of late, stealing users from WhatsApp and gathering millions of others looking for private forms of communication."
 - Canary Security Device - "A complete security system in a single device." Smarter home security starts here. Stay in the know on everything that goes on in your home, even when you're not there. Canary keeps you connected to the people and places that matter most.
- Canon's new security-focused 'SPAD' camera can capture color video in complete darkness - "Designed for applications like security monitoring, it retails for around $25,000. anon has just unveiled the MS-500, an unusual model that's one of the most sensitive non-infrared cameras ever developed. It uses the highest-resolution 1-inch SPAD (Single-photon avalanche diode) sensor yet (3.2 megapixels), and an interchangeable lens mount that allows clear color shooting in light as low as 0.001 lux, according to Canon - less than a clear moonless sky. It's designed to work in 'areas with extremely high-security levels, such as seaports, public infrastructure facilities, and national borders,' the company said."
- CARBON MOTOS CORPORATION - police car E7.
- CARDOK - your own undergorund parking space. Security to protect your car(s).
 - Cardsharp4 - "Black metal credit card folding safety knife." CNC machined from a wafer thin strip of ultralight aluminum including hard anodized surface finish.
- CASTLE SHIPBOARD SECURITY PROGRAM - provides advanced training in shipboard security and vessel defense. The yacht charter industry is one of our primary client categories.
- CCS | COVERT CAMERA SOLUTIONS
- Cellebrite: The FBI got into the Trump rally shooter’s phone in just 40 minutes - "The bureau reportedly used an unreleased Cellebrite tool to open the phone."
- CENTIGON - security vehicles, armored cars, special limousines. World's largest armored vehicle manufacturer and global security systems provider.
- Check if your email has been compromised in a data breach - "Have I Been Pwned allows you to search across multiple data breaches to see if your email address has been compromised."
- CHINAVASION - security equipment from China.
- CHINAVASION - surveillance equipment from China.
- CIA controlled global encryption company for decades, says report - "Swiss government orders inquiry after revelations Crypto AG was owned and operated by US and German intelligence."
- COMPRO TECHNOLOGY - IP cameras, home surveillance.
- Consumer Group Calls Teslas ‘The World’s Most Hackable Cars’ - "Though it’s still not a widespread issue, there remains a growing possibility that your car could be hacked by a cybercriminal in the not-too-distant future. A full 50 million connected vehicles were shipped last year and that number is expected to grow exponentially when 2020 figures are calculated."
- Copenhagen has been named the world’s safest city - "The Danish capital surpassed former frontrunners like Tokyo, Singapore and Osaka in the fourth edition of the EIU’s biennial Safe Cities Index, which for the first time included environmental security metrics."
- COPS PLUS - the source for police supplies, duty gear and tactical police equipment.


- Creative Home Engineering - since 2003. "World's Finest Hidden Passageways." We build custom secret door systems for clients globally, including automated & high security doors. Blending 16 years of award-winning precision engineering with renowned high-security expertise, our team builds the hidden passageways our clients can imagine. Whether a bookcase door, a lifting staircase or a revolving fireplace our team has crafted it. Whether the goal is a wine room entrance, a home theater passageway, or a secret vault door, Creative Home Engineering will achieve it. Our client list spans the globe. Famous builder of secret passageways around the globe, including: bookcase doors, secret vault doors, and secret entrances of all types.
- CREDIT CARD LOCK PICK - it contains 4 of the finest stainless steel picks ever made, and a double-ended tension tool of .035 spring stainless steel. There are 3 cavities in the base of the credit card that hold 2 pairs of picks with the tension tool in the middle. The card set is less than 1/8 inch thick and fits into the same space as a credit card! The Ultimate Spy Gadget!
- Critical Password Warning - 86% Of All Router Users Need To Act Now - "If you are reading this, you are almost certainly doing so without realizing you could be leaving the door open to hackers. New research has revealed that an astonishing 86% of broadband users have little idea about cybersecurity, or at least the security of the device they use to connect to the internet."
- Croma Security SOLUTIONS - "Protecting the things that matter." At Croma we go further to secure the things that matter to you. Whether you need to protect your home, business, people or assets, we are there as your trusted security partner – providing award-winning systems and solutions that deliver the peace of mind and protection you need.
- CROSSMATCH TECHNOLOGIES - global provider of best-in-class, multimodal biometric identity management solutions.
 - Crypto AG - since 1952. "High-security products and
services from a single company. End-user, network & radio security: 25 products, 7 systems, 5 services." Swiss company specialising in communications and information security. The company is a long-established manufacturer of encryption machines and a wide variety of cipher devices.
- CRYPTO MUSEUM - "At present we are a virtual museum in The Netherlands, that can only be visited on the internet. We do, however, regularly organize exhibitions in co-operation with other museums."
- Cute Toy Just Brought a Hacker Into Your Home - The New York Times.
- cyborg cockroaches could be the search & rescue workers of the future - "Cyborg beetles with 'electronic backpacks' could help find disaster victims. Researchers in Australia are fusing control backpacks onto beetles and cockroaches to direct their movements."
 - Cyborg Unplug - "Your defense against wireless surveillance." Anti wireless-surveillance system for the home and workplace. It detects and kicks selected devices known to pose a risk to personal privacy from your wireless network, breaking uploads and streams.
Cyborg Unplug hits wireless surveillance devices where it hurts: network connectivity. 'Plug to unplug', it sniffs the air for wireless signatures from devices you don't want around, sending an alert to your phone when detected. Should the target device connect to a network you've chosen to defend, Cyborg Unplug will immediately disconnect them, stopping them from streaming video, audio and data to the Internet.
A
B
C
D
E
F
G
H
I
J
K
L
M
N
O
P
Q
R
S
T
U
V
W
X
Y
Z
- D -
 - DAMILIC - "The World Leader in Handwriting Automation." Automatic signing machines: Autopen, Signacript and Signature Systems (simulated handwriting software). Read also: Obama's signature: Is it real or is it autopenned?.
- Dark patterns, the tricks websites use to make you say yes, explained - "How design can manipulate and coerce you into doing what websites want."
- DAS SAFE - since 1984. "Anonymous & Non-Anonymous Safes & Data Storage. "There are always things, that you shouldn't have at home". Rent safes per week, per month, or per year. Guaranteed security: 1000 tons of reinforced concrete surround the vault which is protected by a perfect electronic system. In addition the building is guarded day and night. DAS SAFE in Palais Auersperg is located close to the parliament, on Auerspergstrasse 1, at the corner of Lerchenfelder Strasse in 1080 Vienna, Austria.
- DAZZLER (WEAPON) - Wikipedia.
- Default Tech Settings You Should Turn Off Right Away - "These controls, which are buried inside products from Apple, Google, Meta and others, make us share more data than we need to."
- Defence Security and Equipment International | DSEI - since 1999. "The World Leading Defence & Security Event." Defence and security equipment exhibition held every two years in London Docklands, which draws thousands of visitors, both trade and military. It is the world’s largest fully integrated international defence exhibition featuring land, sea and air products and technologies.
- Delivery text scams: the nasty new fraud wave sweeping the UK - "It starts with a text about a fee for a parcel ... and can end with criminals emptying your bank account. Victims and experts explain how to avoid it."
- Digital Fragments We Leave Behind After Death - "The photos, texts, playlists and to-do lists that we find after loved ones die can offer poignant glimpses into their lives."
- digital spring clean: how to sort out your passwords, privacy and bulging photo folder - "From those 6,000 cloud-stored selfies to your most guessable and reused passwords, here is an easy, expert guide to wielding a virtual vacuum."
- DIRECTORY OF SUPPLIERS OF SURVEILLANCE EQUIPMENT
- Does what happens on your iPhone still stay on your iPhone? - "Apple’s famous slogan that suggested total privacy is being tested in the age of AI. Plus: is it time to give up on smartphones all together?"
- Don't Toss Your Old iPhone or Android Smartphone. Turn It Into a Home Security Camera - "Free software can transform your old phone into a basic home security camera. One of the best app options for setting up your phone as a security camera is Alfred. It's cross-platform, so it doesn't matter if your old phone was an Android phone or iPhone. And the same goes for your new phone."
- Don’t use a free VPN - you’ll be putting your data at risk - "With money tight, it’s super tempting to go with a free VPN, right? You really shouldn’t. At least not for long-term use. Sure, some of the best free VPNs could be worth checking out if you’re desperate but for the most part, you really need to sign up to the best VPN that costs money. Once you’ve delved into knowing exactly what a VPN is, it should make a lot of sense why going a paid route is a better option. If you’re still not sure, read on while we break it down for you."
- dos & don’ts of location sharing - "Nearly every app asks for it, but most don’t need it."
- 'doxxing'? A look inside the dark side of the digital world - "With personal data flooding the internet, doxxing - the release of personal information without a person's consent - has become more common. CNN explains what it is, how it happens and hears directly from women who were targeted."
- DPL SURVEILLANCE EQUIPMENT
- Drones With Facial Recognition Are Primed To Fly - But The World Isn’t Ready Yet - "Some of the first drones with advanced facial recognition capabilities are being developed by Israeli surveillance companies, as American police consider whether they will soon be adding the controversial technology to their unmanned flying machines."
- DROPBOX - the easiest way to store, sync, and, share files online. free download.
 - Dropcam Pro WiFi Video Monitoring with Cloud Recording. Setup in Minutes

- Dubai suspected after Princess Haya listed in leaked Pegasus project data - "Closest aides and friends of emir’s ex-wife also began to appear on database as she moved to the UK."
A
B
C
D
E
F
G
H
I
J
K
L
M
N
O
P
Q
R
S
T
U
V
W
X
Y
Z
- E -
- eCONSUMER.GOV - since 2001. "Report international scams online!" econsumer.gov is a partnership of more than 35 consumer protection
agencies around the world. Your complaint helps authorities spot trends and combat fraud.
- Edward Snowden made an app to protect your laptop - The Verge.
- Eight RTX 4090s Can Break Passwords in Under an Hour - "Security researcher Sam Croley took to Twitter to share just how incredible Nvidia's new RTX 4090 really is... at cracking passwords. It turns out it's twice as fast as the previous leader, the RTX 3090, at breaking one of your passwords - even when faced off against Microsoft's New Technology LAN Manager (NTLM) authentication protocol and the Bcrypt password-hacking function."
- ELBIT SYSTEMS - a global defense electronics company.
- Electrician wires van to zap thieves with 1,000-volt shock if they try to break in and police say it’s legal - "An electrician has wired his van so would-be tool thieves get a 1,000- volt shock if they try to break in."
- Eliminalia - "We erase your past we help you build your future." We help you rebuild your future by deleting unwanted and erroneus information and help guarantee your right to anonimity.
- Engadget's Guide to Privacy - "Best practices for keeping your data (and your smart home) safe."
- Eurosatory - International Defence & Security industry trade show that is held every two years in Paris-Nord Villepinte Exhibition Centre, Paris, France.
- Everyone is selling VPNs & that's a problem for security - "The influencer-VPN provider relationship is good for business, but not for security."
- EVERYTHING YOU SHOULD DO BEFORE - AND AFTER - YOU LOSE YOUR PHONE - Wired.
- Experts share their (mostly) hassle-free security tips - "You don't need to post from a digital bunker to stay safe."
- Eye Tap - device that is worn in front of the eye that acts as a camera to record the scene available to the eye as well as a display to superimpose a computer-generated imagery on the original scene available to the eye.
A
B
C
D
E
F
G
H
I
J
K
L
M
N
O
P
Q
R
S
T
U
V
W
X
Y
Z
- F -
- Facebook ‘Secretly’ Tracks Your iPhone Location - This Is How To Stop It - "Facebook has a data addiction - it can’t help itself. The social media giant’s entire business model is built around collecting, processing and then monetizing our personal information."
- Facebook spent $22.6 million to keep Mark Zuckerberg safe last year - "Security costs for the tech billionaire and his family more than doubled last year, as an outcry over Facebook’s practices grew."
- Facial recognition, AI use, surveillance to be enshrined in law - "Monaco’s police force has been using the Principality’s 1,000 CCTV cameras for many years to check on the comings and goings of individuals and vehicles, adding significantly to public security."
- FAKE NAME GENERATOR - "Generate a Random Name." The most advanced name generator. With 30 languages and 22 countries, the Fake Name Generator is the most advanced name generator on the internet.
- Fastvein - "Beyond the fingerprint." The most advanced biometric system in the world providing the equivalent security & accuracy of iris scanning, but at a fraction of the cost.
- FBI urges Olympic athletes to leave personal phones at home ahead of Beijing games - "The FBI is urging Olympic athletes to leave their personal cell phones at home and instead take burner phones to the Beijing Winter Olympics this month, citing the potential for 'malicious cyber activities.'"
- FBI warns consumers not to use public phone charging stations - "The FBI is warning consumers against using public phone charging stations in order to avoid exposing their devices to malicious software. Public USB stations like the kind found at malls and airports are being used by bad actors to spread malware and monitoring software, according to a tweet last week from the FBI’s Denver branch. The agency did not provide any specific examples. 'Carry your own charger and USB cord and use an electrical outlet instead,' the agency advised in the tweet."
- Find out if your iPhone or iPad is infected with Pegasus spyware - "Curious about whether Pegasus has invaded your iPhone or iPad? Here's a way to check for peace of mind."
- ‘Fingerprinting’ to Track Us Online is on the rise. Here's what to do - "Advertisers are increasingly turning to an invisible method that pulls together information about your device to pinpoint your identity."
- FireEye - since 2004. "Cyber Security & Malware Protection." FireEye helps you detect advanced and never-before-seen cyber attacks because it does not rely on signature-based defenses with their barrage of undifferentiated security alerts. By working with FireEye, you can identify connections between alerts, prioritize alerts and get actionable contextual intelligence for rapid remediation.
- Foiling Cyberspies on Business Trips - The New York Times.
- Forensics For Dummies Cheat Sheet - For Dummies.
- Forward this or you’ll die in seven days: On the persistence of chain letters - "They’ve been around forever, and we’ll never get rid of them."
- FRANK M. AHEARN - "The leader in teaching people how to disappear. For over twenty years Frank M. Ahearn has been considered one of the leading skip tracers in the world."
- FRAUD-PROOF CREDIT CARD POSSIBLE BECAUSE OF QUANTUM PHYSICS - University of Twente, Enschede, Netherlands.
A
B
C
D
E
F
G
H
I
J
K
L
M
N
O
P
Q
R
S
T
U
V
W
X
Y
Z
- G -
 - Gate - "The First Camera-Equipped Smart Lock." Gate enhances your deadbolt with a motion-activated camera, keypad, and 2-way audio. Manage everything from your phone.
 - Gego - since 2018. "The golbal tracker for all the things you love." Track your luggage anywhere across the globe. GEGO is a state-of-the-art global tracker that locates all the things you love: kids, purse, bike, car, and valuables! TSA, FAA, IATA Compliant: This GEGO luggage tracker is compliant with all federal and local air travel regulations including TSA, FAA and IATA.
- General Data Protection Regulation (GDPR) - EU Parliament.
- GENERAL DYNAMICS SECTÉRA EDGE SMARTPHONE - Secure Mobile Environment Portable Electronic Device (SME PED).
- Get rid of the paper clutter: how to deal with your household documents - "From ways to store important documents to the right ways to destroy them. That includes things like postage labels you get on a delivery from Amazon, which have your address and details all over them. You need to make sure you take those labels off and destroy them, or alternatively use a thick marker pen to obscure the details."
- GF PROTECTION - intelligence & safety.
- GILARDONI - X-ray and ultrasonic solutions for security, medical diagnostics, non-destructive testing (NDT) and OEM components.
- GLARE MOUT - non-lethal visual disruption laser by B.E. Meyers Electro Optics.
- go bag: Everything you need to prepare for wildfires, earthquakes, hurricanes & tornadoes, according to experts - "Here is a round-up of emergency supplies and preparation resources, including recommendations from experts as well as a selection of gear we’ve tested ourselves."
- go bag: What to pack in a ‘go bag’ for when disaster strikes - "When wildfires rage, hurricanes bear down, flood waters rise and that big earthquake finally strikes, it’s critical that you and your family members are ready to evacuate. A basic emergency supply kit should include: One gallon of water per person, per day, Three-day supply of non-perishable food per person and per pet."
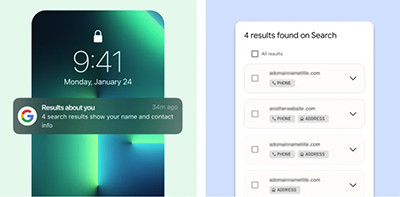 - Google can now alert you when your private contact info appears online - "You can receive notifications when your address, phone number, or email pops up in its search results."
- Google Confirms Gmail To Ditch SMS Code Authentication - "It is certainly no secret that using SMS text messages for security codes used to authenticate your identity is far from ideal. Gmail is to ditch the use of SMS codes for authentication purposes, a Google spokesperson said. Here's what you need to know."
- Google Nest Smoke Detector review with HomeKit - "Does Google make the best smart smoke detector once added to HomeKit?"
- Google now has its own hardware security keys - "They're more secure than traditional two-factor authentication methods."
- GOOGLE SHARING - how to hide from Google. A special kind of anonymizing proxy service, designed for a very specific threat. It ultimately aims to provide a level of anonymity that will prevent google from tracking your searches, movements, and what websites you visit.
- Guide: Extreme online security measures to protect your digital privacy - The Guardian.
- Guide to digital security - Wired.
A
B
C
D
E
F
G
H
I
J
K
L
M
N
O
P
Q
R
S
T
U
V
W
X
Y
Z
- H -
- Hack Brief: 'Devil's Ivy' Vulnerability Could Afflict Millions of IoT Devices - Wired.
 - Hacking Team - "Here in HackingTeam we believe that fighting crime should be easy: we provide effective, easy-to-use offensive technology to the worldwide law enforcement and intelligence communities. Technology must empower, not hinder. Exclusively focused on offensive security, HackingTeam was founded in 2003. In 2004, we were the first to propose an offensive solution for cyber investigations, with such a strong reception that in 2007 we were venture backed. All the development is made in Milan, by a team of 50+ professionals focusing on all the aspects of offensive security, Our technology is used daily to fight crime in six continents."
- HART SECURITY - land, sea & air security.
- Here’s how to check your phone for Pegasus spyware using Amnesty’s tool - "The process involves some terminal work, but it’s relatively straightforward."
- Here's how to protect against iPhone password reset attacks - "One of the latest attacks on iPhone sees malicious parties abuse the Apple ID password reset system to inundate users with iOS prompts to take over their accounts (often called 'MFA bombing')."
- Here’s How You Can Protect Yourself From Increasingly Sophisticated Cybercriminals - "With cybercriminals becoming more sophisticated, it’s important to understand the types of fraud out there. We spoke to two cybersecurity and identity theft experts to walk you through how to protect yourself and what to do if your credit card (or debit card) information is stolen."
- HIDDEN CAM - videos, equipment, & reviews.
- hidden fingerprint inside your photos - "They say a picture is worth a thousand words. Actually, there's a great deal more hidden inside the modern digital image."
- HIDDEN SPY COMPANY - spy cameras.
- Hong Kong: This city is getting thousands more CCTV cameras despite being among the world’s safest. Why? - "Hong Kong plans to install thousands of surveillance cameras. Critics say it’s more proof the city is moving closer to China."
- How a cosmetics bag left thousands of passengers in the lurch at Munich Airport - "It was a striking example of how no risks are taken when it comes to airport security in the 21st century. a mishap involving a cosmetics bag led to 30,000 passengers being stranded in Munich - many of whom have been left out of pocket."
- How can US law enforcement agencies access your data? Let’s count the ways - "A hack using a forged legal request that exposed consumer data collected by Apple and Meta shed light on the reach of the law."
- How do I protect my online privacy from 'surveillance capitalism'? - "On Monday, the Electronic Frontier Foundation published a 17,000-word report on this topic. Behind the One-Way Mirror: A Deep Dive Into the Technology of Corporate Surveillance, by Bennett Cyphers and Gennie Gebhart, covers both online privacy problems and the growth of real-word surveillance."
- How do the rich & famous protect their homes? - BBC News.
- How Hackers Use Power LEDs To Spy On Conversations 100 Feet Away - "If you thought hackers being able to make use of any ordinary light bulb to spy on your conversations from 80 feet away was ingenious, wait until you see what they have come up with now."
- How Many Times Has Your Personal Information Been Exposed to Hackers? - "There’s been another mega-breach. Marriott said Friday that information for as many as 500 million of its customers may have been stolen. Answer the questions below to learn which parts of your identity may have been stolen in the last five years. Not all attacks are included here, and many attacks go undetected, so think of your results as a minimum level of exposure."
- How New Zealand became an apocalypse escape destination for Americans - "In Queenstown - a picturesque ski spot that often attracts comparisons to Aspen, Colorado - rumors about foreigners investing in apocalypse-proof bunkers have been swirling for years."
- how smart devices are outsmarting criminals - The Guardian.
- How Spy Tech Firms Let Governments See Everything on a Smartphone - The New York Times.
- How the colour of your swimsuit can save your life - "Colours change to a surprising degree when submerged underwater, so what you and your children wear in the water can make a difference in an emergency."
- How to arrange for your digital legacy - "What happens to your online stuff when you’re no longer around?"
- How to avoid being kidnapped abroad (by someone who was) - The Telegraph.
- How to blur sensitive information in images on your iPhone, iPad, or Mac - "If you're looking to share a screenshot or photo, but you don't want to expose anything too personal, here's how you can blur or otherwise censor them on your Mac, iPhone, or iPad."
- How To Check If Your Apple Watch Is Infected With Spyware - "When your watch is a sophisticated computing device, it’s also a target for hackers. Now you can scan your Apple Watch for spyware; here’s how."
- how to check your phone for Pegasus spyware using Amnesty’s tool - "The process involves some terminal work, but it’s relatively straightforward."
- HOW TO ENCRYPT ALL OF THE THINGS - Wired.
- How to increase your privacy in Chrome, Firefox & Safari - The Verge.
- How to Keep Your Zoom Chats Private & Secure - "Trolls. Prying bosses. Zoom's a great video chat platform, but a few simple steps also make it a safe one."
- How To Lock Any iPhone App Behind Face ID, Touch ID, or a Passcode - "Give certain apps an extra layer of security protection. Tap on New Automation if you haven't previously created any automation or the + (plus) button in the top right corner if you have. From the list that pops up, select App, then on the next screen, tap on Choose to pick the app(s) you want to lock away - you can choose more than one, if necessary."
- How to pay for things securely - "Make sure the only person buying stuff with your money is you."
- How to permanently erase data on hard drives, SSDs, & flash drives - "Time and again, cases are reported in which disposed hard drives still contained readable, confidential data. With a few Windows commands and the right tools, this won't happen to you."
- How to Protect Your Digital Privacy - "Protestors should be mindful of the data they generate before headed to a demonstration—police can issue warrants for a person’s search history, chat logs and social media posts, experts say. (Social media companies, including Facebook, have dedicated pages for police 'to gather evidence in connection with an official investigation,' giving the police an easy way to access information.)"
- How to Protect Your Smart Home From Hackers - "Smart home devices can make life more convenient, but may put you at risk of being hacked. Ensure your safety with a few simple measures."
- HOW TO SECURE YOUR ACCOUNTS WITH BETTER TWO-FACTOR AUTHENTICATION - Wired.
- How to secure your phone before attending a protest - "If you’re attending or even just watching the protests, then be aware: not only is your phone a trove of information about you and the people you communicate with, but it also functions as a tracking device. That’s why it’s important to keep your digital footprint as small as possible - any evidence placing people at protests could be enough to get them arrested. You should account for the fact that your phone may get lost, stolen, or broken. There’s also a risk of your phone being confiscated by authorities - which means that if they’re able to unlock your phone, they’ll have access to data on you and people you know. In other words, it never hurts to prepare for the worst, especially considering recent events. The steps we’ve listed here are a basic start toward protecting your privacy before you attend a protest."
- How to Send Secret Encrypted Messages Using Your iPhone Notes App - "You can send and receive secret messages straight from your iPhone. The built-in Notes app for iOS is a secret weapon for private conversations."
- How to set up two-factor authentication on all your online accounts - "An extra step of security never hurt anybody."
- How to Share Your Online Accounts the Safe Way - "Be generous, but also be careful."
- How to spot the software that could be spying on you - "Research suggests that proliferation of stalkerware is a growing problem: A study by Norton Labs found that the number of devices indicating that they had stalkerware installed rose by 63% between September 2020 and May 2021."
- How to stay safe online: 15 ways to avoid being hacked - The Telegraph.
- How to stop your bicycle from being stolen - "Don’t buy an amazing bike, keep it indoors and use two lock."
- How to stop your smart home spying on you - "Everything in your smart home, from the lightbulbs to the thermostat, could be recording you or collecting data about you. What can you do to curb this intrusion?"
- How to Survive Airport Security - The New York Times.
- How to Tell a Secret in the Digital Age - The New York Times.
- How to use Apple TV’s picture-in-picture mode to view a HomeKit camera feed - "Watch your home security camera while watching TV."
- How to use Philips Hue’s new smart security system - "Philips Hue just added new security features to its smart lighting line, and you can turn them on for free."
- How to use secret codes on iPhone - "Here's how to use secret codes on iPhone and open up new features by dialing a few numbers."
- How to use the iOS app tracking blocker - "Apps have to ask your permission to track you during installation."
- How to use your iPhone & AirPods to spy on people - "An iPhone and AirPods can be used to listen to conversations without people knowing. Such iPhone spying is really just a tricky use of the Live Listen feature built into iOS. And, even if you’re not a budding James Bond, knowing about this trick could keep someone from eavesdropping on you. Here’s what to do if you want to use your iPhone to spy on someone. (Or what to watch out for if you don’t want to fall victim to iPhone spying.)"
- How to use your phone to find hidden cameras - "If the camera is using an infrared light, your phone can pick up what your eyes can’t."
- How Your Car Watches Everything You Do & Everywhere You Go - "To determine what state the driver was in, the Tennessee Highway Patrol stepped in and determined that they should look at data from the airbag control module (ACM). This hidden part of the car records the approximate speed, the braking and the amount of throttle used by the driver. The police wanted to know what was happening before and during impact. The ACM is just one of many modules that records what’s happening in a vehicle at any one time."
- Hue Secure: The new security system from Philips Hue - "Cameras and contact sensor in detail. This week Philips Hue will present its new surveillance system called “Hue Secure”. In the past few weeks, a lot of information has already leaked out. I would like to provide you with the most important details shortly before the official presentation and also give you some assessments."
A
B
C
D
E
F
G
H
I
J
K
L
M
N
O
P
Q
R
S
T
U
V
W
X
Y
Z
- I -
- I just discovered my Roomba can be a security camera - "iRobot’s new Remote Check In feature lets you access the camera on the j7 Roomba, so you can see a live view of your home."
- ID-Art mobile app - Interpol - "Our first-ever app, called ID-Art, uses cutting-edge image-recognition software to help identify stolen cultural property, reduce illicit trafficking, and increase the chances of recovering stolen items."
- If Jeff Bezos’ iPhone Can Be Hacked Over WhatsApp, So Can Yours - "How is it that even the richest man in the world can have his phone hacked with a simple WhatsApp message?"
- IMS SECURITY - offers Israeli style security services and tactical training. Specializing in protecting Hollywood actors and providing tactical training.
- IMSI catcher - an IMSI catcher (International Mobile Subscriber Identity) is a telephony eavesdropping device used for intercepting mobile phone traffic and tracking movement of mobile phone users.
- Inside $10 Million Luxury Underground Bunkers - "Inside Oppidum’s Luxury Underground Residences Where The Ultra-Wealthy Plan On Living Out The End Of The World."
- INTERNATIONAL ARMORED GROUP - custom armored vehicle builder.
- INTELIUS - "Live in the know." Pioneers in the information commerce industry, innovating technologies to collect, interpret and deliver information to consumers and businesses online. Advanced people search in the U.S. Background check. Reverse cell phone lookup.
- INTERNATIONAL SECURITY ACADEMY - "Our programs include 4 focal areas: 1. Close Protection, 2. High Risk Protection, 3. Maritime Protection, 4. Protection & Counter Terrorism Instructors. The International Security Academy's' activities are recognized, authorized and supervised by the State of Israel and other countries where our practical training centers are activated."
- International Spy Museum - since 2002. Washington, DC, U.S.A. The Museum features the largest collection of international espionage artifacts ever placed on public display. It is the only public museum in the United States solely dedicated to espionage and the only one in the world to provide a global perspective on an all-but-invisible profession that has shaped history and continues to have a significant impact on world events.
- iOS 14: Here’s Why There’s An Orange Dot On Your iPhone - "Since upgrading to iOS 14, have you noticed a orange dot at the top right hand side of your iPhone? You are not alone - this is actually a new feature and don’t worry, it is intentional. So what is it? Apple’s new iOS 14 operating system update comes with a huge focus on security and privacy. As part of its new iPhone update, Apple has added an indicator light that tells you when an app is using your microphone and camera, and this comes in the form of an orange or green dot. It sounds scary but seeing the dot at the top of the screen is not a reason to be alarmed in all cases. Some apps need to use your microphone (orange dot) or camera (green dot) in order to function - your phone for example, or a video conferencing app such as Zoom, WhatsApp, or Signal."
- iOS 17.5, iPhones can now notify you when unauthorized trackers are following you - "The goal of this new Apple update is to eliminate unwanted trackers. A new industrial specification devised by Apple and Google to address security risks of Bluetooth tracking devices is now available."
 - IOSAFE - "Disaster proof hardware." Go-Anywhere ioSafe Rugged Portable Hard Drive.
- IRONKEY - the world's most secure flash drive.
- iPhone: Does what happens on your iPhone still stay on your iPhone? - "Apple’s famous slogan that suggested total privacy is being tested in the age of AI. Plus: is it time to give up on smartphones all together?"
- iPhone trick cheaters are OBSESSED with: 'It's much harder to spot' - "'It's the humble Notes app. Yes, the same place you pop groceries lists and all those draft angry texts to your ex. In the Notes app, you can invite people to collaborate in real time on a note in iCloud, and everyone who has access can see the latest changes."
- iPhone ‘Weak Security’ Wi-Fi Warning: Here’s What It Means - "Have you received a 'weak Wi-Fi security' warning on your iPhone since upgrading to iOS 14? You are not alone, here’s what it means and how to fix it."
- Is Your Driving Being Secretly Scored? - "The insurance industry, hungry for insights into how people drive, has turned to automakers and smartphone apps like Life360. You know you have a credit score. Did you know that you might also have a driver score? The score reflects the safety of your driving habits - how often you slam on the brakes, speed, look at your phone or drive late at night."
- Israel tried to frustrate US lawsuit over Pegasus spyware, leak suggests - "Officials seized documents from NSO Group to try to stop handover of information about notorious hacking tool, files suggest."
- It Outage: Widespread technology outage disrupts flights, banks, media outlets & companies around the world - "A global technology outage grounded flights, knocked banks offline and media outlets off air on Friday in a massive disruption that affected companies and services around the world and highlighted dependence on software from a handful of providers."
A
B
C
D
E
F
G
H
I
J
K
L
M
N
O
P
Q
R
S
T
U
V
W
X
Y
Z
- J -
- J.A. HARKINS CUSTOM KNIVES
- JANE'S INFORMATION SOLUTIONS - intelligence and insight you can trust.
- JIANGSU ANHUA POLICE EQUIPMENT MANUFACTURING CO. - anti-riot suits, handcuffs, police batons, traffic, extendible, retractile and electric batons, bulletproof vests, road blocker, fetters, body armor, duty leather/security belt, Normex masks, metal detectors, traffic baton, tactical goggles.
- Junk mail: how one click can lead to a deluge - "When piles of unsolicited mail and catalogues thud through the letterbox, ask yourself: how do they get your details and how can you stop it?"
A
B
C
D
E
F
G
H
I
J
K
L
M
N
O
P
Q
R
S
T
U
V
W
X
Y
Z
- K -
- KABA ILCO - a worldwide leader and innovator in providing electronic hotel lock solutions. Key systems. Access control.
 - KENSINGTON LOCKS - "World's #1 Seller of Laptop Locks." Arm your business with the first line of defense against laptop, equipment and data theft. Kensington security locks are convenient and easy for employees to use-whether they're in the office or on the go.
- KGB CAMERAS - wireles and CCTV video cameras.
- Krebs on Security - "In-depth security news and investigation."
- Kroll - corporate investigations and risk consulting firm based in Midtown Manhattan, New York City. It was established in 1972. It is the world's leading risk and security consultancy.
-
A
B
C
D
E
F
G
H
I
J
K
L
M
N
O
P
Q
R
S
T
U
V
W
X
Y
Z
- L -
- LAS VEGAS RESORT USING MICROWAVES TO KEEP GUNS OUT OF ITS CASINO - Wired.
- LASER DAZZLER - LE Systems Inc.
 - Le Freeport - "A high-end, ultra safe facility for the storage of valuable goods." LE FREEPORT sets new standards, demanded by investors and collectors alike: a purpose built facility combining cutting edge technology, efficient logistics, and an exhaustive range of expert services. LE FREEPORT is the ideal platform for securing, servicing and selling works of art and other valuables. Luxembourg & Singapore.
- Lie detection systems go high-tech - "Methods of lie detection have probably been around for as long as tall tales have been told. One of the first documented examples comes from 1000BC in China, where a suspect would have to fill his or her mouth with dry rice. The early 20th Century saw the invention of the first lie detection machines or polygraphs. The most well-known of these is the "analogue polygraph", which typically has three or four ink-filled needles that dance round on a strip of moving paper."
- LIFEGUARD - "Be Smart. Be Safe. Get LifeGuard Personal Breathalyzer." The LifeGuard breath alcohol tester is a high quality device to help you manage your Blood Alcohol Content (BAC). The LifeGuard breathalyzer uses the same fuel cell technology as Law Enforcement instruments, giving you the most accurate BAC readings to help you manage your BAC.
- Lightning security key for iPhones is here, and it works with USB-C, too - "If you’ve wanted to just plug a physical security key into your iPhone to log into apps securely - instead of problematic text messages or paging over to your authenticator app - now you can. Today, Yubico is releasing the $70 YubiKey 5Ci, the first security key that can plug into your iPhone’s Lightning port or a USB-C port, and it’s compatible with popular password vaults LastPass and 1Password out of the box."
- LIST OF HANDCUFFS MANUFACTURERS
 - Lookout - "The best mobile security for individuals and enterprises alike." Lookout gives you a fighting chance of getting your lost or stolen phone back, whether it’s in the couch cushions or lost after a night out.
- LOOMIS - managing cash in society.
- LORRAINE ELECTRONICS - manufacturer and distributor of covert electronic surveillance equipment.
- LWRC INTERNATIONAL - reliable tools for the warfighter, law enforcement professional and civilian shooter.
A
B
C
D
E
F
G
H
I
J
K
L
M
N
O
P
Q
R
S
T
U
V
W
X
Y
Z
- M -
- Man watches from his phone as robbers break into his apartment - New York Post.
- Mastering Bitcoin: Unlocking Digital Cryptocurrencies
 - essential reading for everyone interested in learning about bitcoin basics, the technical operation of bitcoin, or if you're building the next great bitcoin killer app or business. From using a bitcoin wallet to buy a cup of coffee, to running a bitcoin marketplace with hundreds of thousands of transactions. - essential reading for everyone interested in learning about bitcoin basics, the technical operation of bitcoin, or if you're building the next great bitcoin killer app or business. From using a bitcoin wallet to buy a cup of coffee, to running a bitcoin marketplace with hundreds of thousands of transactions.
- Meet the man building bunkers for billionaires - "They are thousands of miles from conflict zones, but these home-owners are still prepping for Armageddon."
- MICRO SURVEILLANCE EQUIPMENT
- Milipol - since 1984. "Worldwide exhibition of internal State security." The world’s leading security exhibition.
- Millions Of Apple Users Warned To Delete ‘Very Malicious’ Hidden Files - "An alarming warning has just been issued for millions of Apple users, after a 'very malicious' malware was found stealing credentials, logging keystrokes and recording screenshots. Here’s what you must do today."
- MINOX DSC DIGITAL SPYCAM - "License to Shoot." Seeing this camera makes people immediately think of Bond, James Bond, and not without good reason. The DSC is small, really small. It’s so tiny it disappears in a clenched fist. Just 86 × 29 × 20 mm. 5.1 megapixel CMOS Sensor.
- MOLKA - in South Korea, molka are miniature cameras secretly and illegally installed in order to capture voyeuristic images and videos. Spy cameras proliferated in the country in the 2010s and are most commonly installed in small holes or cracks in walls in locations such as women's public restrooms and motel rooms. The voyeuristic images and videos are sold online across various platforms, including popular social media sites like Twitter and Tumblr, without knowledge or consent of those on camera.
- Most Dangerous & Safest Countries Index - "Travel Safe - Abroad. Click on the name of the country to see more information regarding its safety."
- MyOneSpy - "Cell Phone Spy Software to Track & Monitor Mobile Phones & Tablets." Offering an undetectable cell phone spy software to track and monitor any Android, Blackberry, iPhone and tablet.
A
B
C
D
E
F
G
H
I
J
K
L
M
N
O
P
Q
R
S
T
U
V
W
X
Y
Z
- N -
- Nest Cam IQ Outdoor camera use facial recognition - The Verge.
 - Nest Protect - "We made a smoke and CO alarm you’ll love, because hating it is dangerous."
- Nest takes on home defense with its Secure alarm system - engadget.
 - Netatmo Presence - "Outdoor Security Camera with People, Car and Animal Detection." Prevent break-ins or damage on your property. Ultra-precise alerts let you know instantly about what happens outside your home. Use live stream to view your property in real-time. At night, either watch discreetly with Presence's infra-red night vision or switch the camera's floodlight on. The smart floodlight can be switched on manually in the app or set to switch on when it detects a person, car or animal - or for all three. It helps you find your way safely at night and deters any unwanted visitors.
 - Netatmo Welcome - "Home Security Camera with Face Recognition." Sends the names of the people it sees directly to your smartphone. Be notified when your children or elderly parents are home. The security camera also alerts you when it sees a stranger.
- New Critical Password Warning - 86% Of All Router Users Need To Act Now - "If you are reading this, you are almost certainly doing so without realizing you could be leaving the door open to hackers. New research has revealed that an astonishing 86% of broadband users have little idea about cybersecurity, or at least the security of the device they use to connect to the internet."
 - Nimb - "Smart Ring That Helps You Feel Safe & Sound." The ring with a panic button to send an alert to friends & family, emergency services, community members & people nearby.
- Now Is a Good Time to Update Your Recovery Email Addresses - "You know those 'emergency' email addresses you can use to get into your email and other accounts in case you're locked out? Make sure they're up-to-date."
A
B
C
D
E
F
G
H
I
J
K
L
M
N
O
P
Q
R
S
T
U
V
W
X
Y
Z
- O -
- OK gesture - the OK or ring gesture is performed by connecting the thumb and index into a circle, and holding the other fingers straight or relaxed away from the palm. Commonly used by divers, it signifies "I am OK" or "Are you OK?" when underwater. In most English-speaking countries it denotes approval, agreement, and that all is well or "okay". In other contexts or cultures, similar gestures may have different meanings or connotations including those that are negative, offensive, financial, numerical, devotional, political, or purely linguistic.
- One man lost his life savings in a SIM hack. Here's how you can try to protect yourself - "Robert Ross was sitting in his San Francisco home office in October 2018 when he noticed the bars on his phone had disappeared and he had no cell coverage. A few hours later, he had lost $1 million."
- Online Safety Tips for Kids & Parents - "Best Internet Privacy Guide 2020. As valuable as the internet can be in our lives, it can also be a dangerous place. You’ll have to look carefully at how well you’re going to handle your online activities if you want to do things in this vast landscape."
- Online tracking - A 1-million-site measurement and analysis Draft: July 11th, 2016. Princeton University.
- ONPOINT TACTICAL - "Legendary Skills for Today's Professionals." Offers superior training for military, law enforcement, and select professionals & civilians who require advanced outdoor skills.
- Oppidum - since 2015. "ULTRA-LUXURY FORTIFIED UNDERGROUND RESIDENCES." We are an engineering, technology and development company specializing in ultra-luxury fortified underground residences. We create spaces that are totally secure and utterly discreet yet sumptuously appointed and entirely bespoke - all underground, within your own domain. You can be sure that you, your family and your most treasured possessions have a place of safety and comfort close at hand for as long as you need, whatever happens in the world outside.
- OPTOELECTRONICS - manufactures and distributes test equipment, receivers, and frequency counters for use in the scanning hobby, commercial radio, and law enforcement.
- OPTOSECURITY - OptoSreener: designed as a first-line detection system aimed at preventing terrorist events or attacks that may occur in high-profile and critical facilities (e.g. airports).
 - Osdin Shield - "Protection Furiture." We design, create and build, unique, bespoke, ballistic resistant furniture.
- OVERPLAY - "By rerouting your internet connection through our worldwide VPN servers you can: change your IP address to one in another country; improve your security by ensuring your internet traffic is encrypted; access content that is normally restricted at your location."
A
B
C
D
E
F
G
H
I
J
K
L
M
N
O
P
Q
R
S
T
U
V
W
X
Y
Z
- P -
- Pacsafe - "Smart Travel Gear." Anti-Theft Travel Bags and Travel Accessories.
- Paramedics Share One Tip That May Save Your Life - "Every second counts, experts say: Step one: Write down your details. Step two: Keep the sheets somewhere that's easy to find."
- Passkeys: all the news & updates around passwordless sign-on - "The need to remember lengthy, complicated passwords to sign into your accounts could soon be a thing of the past thanks to passkeys: a new login technology that replaces passwords with authentication mechanisms built into your own devices. That means you can use Face ID on your iPhone, Windows Hello on your PC, or the fingerprint sensor on your Android phone to authorize access to your websites, apps, and services - providing they support passkey sign-on."
- Password Meter - How Secure is my Password? Free Online Tool - SafetyDetectives.
- Pegasus - since 2016. Spyware developed by the Israeli cyber-arms company NSO Group that is designed to be covertly and remotely installed on mobile phones running iOS and Android.
- Pegasus scandal: Are we all becoming unknowing spies? - "The allegations that spy software known as Pegasus may have been used to carry out surveillance on journalists, activists - and even perhaps political leaders - highlights that surveillance is now for sale."
- Pegasus Spyware: Does Apple Have ‘Major’ iMessage Security Problems? - "iPhone spyware made by $1 billion surveillance company NSO has exposed 'major' issues in Apple iMessage security, according to a security expert who has spent years researching the Israeli business’ hacks."
- PEOPLE SEARCH PRO - free people search, search people, phone numbers, or public records for free.
- PEOPLE SMART - people search & background checks by name, phone, email or address. Find contact information, social networking data, and public records in a way that respects privacy.
- Philips Hue's new security cameras leak in FCC filings - "Two of the four rumored models have now been approved by the FCC, giving us a glimpse at the camera’s specs and cylindrical design."
- Phishing scams leveled up, and we didn’t - "Don’t be Jeff Bezos."
- Phone Hacks Can Happen to Anyone. Here’s How to Protect Yourself - "Start by knowing what could expose you to an attack, like vacation clues, hotel Wi-Fi and inadequate verification procedures."
- PHONE NUMBERS WERE NEVER MEANT AS ID - Wired.
- Pick-Pocket Proof | Travel Clothing - "Clothing Arts: Innovating Travelwear Since 2009."
- PimEyes: Face Recognition Search Engine & Reverse Image Search - since 2017. "PimEyes is an online face search engine that goes through the Internet to find pictures containing given faces."
 - Piper - "Smart, elegant security and home automation." Home security and automation device with HD camera, environmental sensors, and Z-Wave home automation abilities.
- PLASTIC HANDCUFFS
 - POLY-CONTROL - "Bulding and Home Control." Specialists when it comes to wireless solutions for your buildings or private homes. The solutions are 100% wireless, installed easily by you. The products are sold through resellers all over the world.
- PRIVACY INTERNATIONAL - founded 1990. Surveillance and privacy watchdog.
- Privacy phone wars: Boeing Black vs. the Blackphone vs. Snowden Phone - SiliconANGLE.
- Privacy Policy: Here’s What You’re Actually Agreeing To When You Accept a Privacy Policy - "Almost every new app or product that is connected to the internet forces you to accept a long, indecipherable privacy policy in order to use it. These documents outline the company’s data-collection practices. But what exactly are you agreeing to when you accept?"
- Products That Do & Don’t Protect Your Phone - The New York Times.
- Proof of Existence - Provides Intellectual Property Rights. Can be used to demonstrate document ownership without revealing the information it contains, and to provide proof that a document was authored at a particular time. The key advantages are anonymity, privacy, and getting a decentralized proof which can't be erased or modified by anyone (third parties or governments).
- Protect Your Credit Card by Changing This iPhone Setting - "If your iPhone's case holds your credit card, you should tweak this setting now: 1. Tap Settings. 2. Tap Face ID & Passcode. 3. Enter your Passcode. 4. Under Allow Access When Locked, tap the slider next to Reply with Message. Now when you receive a text, you'll need to unlock your phone to reply."
- PSIPHON - web proxy designed to help Internet users securely bypass the content-filtering systems used to censor the internet by governments in places like China, North Korea, Iran, Syria, Myanmar, Saudi Arabia, and others.
A
B
C
D
E
F
G
H
I
J
K
L
M
N
O
P
Q
R
S
T
U
V
W
X
Y
Z
- R -
- RANSOM NOTES - Ransomware funds more ransomware, so how do we stop it?
 - Ray-Ban Stories - "The New Way To Capture, Share & Listen." In partnership with Facebook, discover our first generation of smart sunglasses and eyeglasses that keeps you connected. So you can keep your eyes on the world around you.
 - Rhanders - founded in 1811. ANTI-BACTERIAL TECHNOLOGY. "For more than 200 years we have been at the forefront with innovation that can improve our gloves. This is a selection of styles that prevent bacteria on your hands and thereby protect your health." Men's & women's.
- ROBERT WITTMAN INC. - security, protection and recovery of your art investments.
- Russian face recognition company that could end public anonymity is going global - Fusion.
A
B
C
D
E
F
G
H
I
J
K
L
M
N
O
P
Q
R
S
T
U
V
W
X
Y
Z
- S -
- Safe room - or panic room is a fortified room that is installed in a private residence or business to provide a safe shelter, or hiding place, for the inhabitants in the event of a break in, home invasion, tornado, terror attack, or other threat. Safe rooms usually contain communications equipment, so that law enforcement authorities can be contacted.
- safest countries in the world to visit in 2020 - "For those who are planning a holiday for next year and wondering which countries are the safest, a risk map published by an organization specializing in travel security may be of help."
- Safety first: the short, simple guide to securing all your passwords - "If you log in to every website with the same details, you’re doing it wrong. Here are four easy steps to unhackability."
- SANYO CCTC SYSTEM - CCTC security systems.
- SAVELEC - aims to provide a solution for the external, safe control of a non cooperative vehicle without any consequences on the persons inside the vehicle or other persons and objects nearby.
- SECOND CHANCE ARMOR - the first one to use kevlar for body armor.
- Secret Doors Are Having a Major Moment - "Not Just for Scooby-Doo Anymore - the Secret Door Is Having a Moment. Homeowners are adding hidden doors and rooms to foil burglars, eke out extra storage space and prepare for Armageddon."
- secret iPhone trick cheaters are OBSESSED with: 'It's much harder to spot' - "'It's the humble Notes app. Yes, the same place you pop groceries lists and all those draft angry texts to your ex. In the Notes app, you can invite people to collaborate in real time on a note in iCloud, and everyone who has access can see the latest changes."
- Secure Mobile Apps - The Guardian Project.
- Secure Passwords 101 - "Why They Matter + How To Create Them."
- SECURESAFE PRO - password and credit card manager software.
- Security camera: Turn an Obsolete Phone Into a Free Security Camera With 3 Easy Steps - "If you're replacing your iPhone or Android phone, we've got the perfect idea for your old model: Turn it into a free home security camera with the right app."
- Security cameras can tell burglars when you're not home, study shows - "Some popular home security cameras could allow would-be burglars to work out when you've left the building, according to a study published Monday."
- SECURITY CAMERAS DIRECT
- SECURITY MAGAZINE - solutions for enterprise security leaders.
 - Selecta DNA - "Advanced Forensic Marking." Reduces burglaries by up to 83%. By using SelectaDNA to mark your property with a unique DNA identifier, we can help you protect your home or business, so that you don’t become a victim too. Protecting your home with SelectaDNA makes you less likely to be burgled. In fact, 93% of UK Police Forces have used SelectaDNA to bring down crime.
 - Shonin Streamcam Wearable Camera - "Capture YOUR side of the story." Simplifies personal security. It'll broadcast directly to Facebook Live & YouTube.
- Should you keep using WhatsApp? Plus five tips to start the year with your digital privacy intact - "We spoke to convicted hacker turned security consultant Kevin Mitnick to find out how to maintain your security online."
- Sign Documents on Your iPhone in Just 5 Easy Steps - "Printer ink is expensive, so here's how to save yourself the hassle: 1. Open Files. 2. Tap the document you want to sign. 3. Tap the icon across the bottom of your screen that looks like a pen tip in a circle. 4. Tap Add Signature. 5. Sign your name on this new screen with your finger then tap Done."
- Signal, WhatsApp & Telegram: Here's which secure messaging app you should use - "Looking for a more secure messaging app? We break down the key differences between three of the most popular apps, including the one Elon Musk recommends."
- Smartphone app can detect hidden camera lenses from reflections - "Time-of-flight sensors built into some smartphones can be used to detect the telltale reflections from hidden camera lenses."
- SMARTPHONE SECURITY 101: THE STEPS THAT MATTER MOST - Wired.
- Smartphone tracking: Is your smartphone being tracked? Here’s how to tell - "An expert in digital forensics and family violence says surveillance by spyware is rare - more often it happens via everyday features such as location sharing."
- Smishing: How to steer clear of Smishing Scams - "What Is a Smishing Scam and How to Stay Safe. Smishing can be particularly convincing, posing as a FedEx carrier, bank, or other known entity. Since the scam happens via text, people may be particularly vulnerable to them."
- SMITH & WARREN - "Custom Badges manufactored in 3 weeks!".
- SMITH & WESSON - since 1852. Firearms, knives, handcuffs, accessories, and more.
- Snowden Designs a Device to Warn if Your iPhone’s Radios Are Snitching - Wired.
- Solid - since 2016. "Solid: Your data, your choice. Advancing Web standards to empower people." Solid (Social Linked Data) is a web decentralization project led by Sir Tim Berners-Lee, the inventor of the World Wide Web. The project "aims to radically change the way Web applications work today, resulting in true data ownership as well as improved privacy" by developing a platform for linked-data applications that are completely decentralized and fully under users' control rather than controlled by other entities. The ultimate goal of Solid is to allow users to have full control of their own data, including access control and storage location.
- sousveillance - definition & explanation.
 - SpiderOak - since 2007. "Store. Sync. Share. Privately." SpiderOak makes it possible for you to privately store, sync, share & access your data from everywhere. US-based online backup tool to back up, share, sync, access and store data using an off-site server. The software uses encrypted cloud storage and client-side encryption key creation, so even employees of SpiderOak cannot access users' information. In a July 2014 interview, former NSA contractor Edward Snowden recommended SpiderOak over Dropbox, citing its better protection against government surveillance.
- Spies, lies & data thieves: It's time to get a VPN - "Cover your assets."
- SPY GADGET WAREHOUSE - "Satisfy Your Inner Spy."
- 'Spy pixels in emails have become endemic' - "The use of 'invisible' tracking tech in emails is now 'endemic', according to a messaging service that analysed its traffic at the BBC's request."
- SPYMODEX - cell phone jammer, detectors, and other gadgets.
- Spyware leak suggests lawyers & activists at risk across globe - "Leaked records show dissidents and those who help them prominent among those under threat from NSO spyware."
 - STABIQ TREASURE HOUSE - "Your Safest Place." In times of swift political and social change and increased uncertainty on the financial markets, there is a growing desire for safety and consistency. Our Asset Protection Solutions offer our customers sustainable and reliable solutions as well as a safe haven. In collaboration with our attorney and trust company, we offer the opportunity of storing your valuable items such as gold and precious metals, works of art, jewellery, watches and coin collections in exclusive surroundings within an area of over 6000 m². At the same time, valuables can be presented, viewed and evaluated in our exclusive showrooms. The STABIQ Treasure House is also an Open Customs Warehouse (OCW) managed in accordance with the strict guidelines of the Swiss Customs Authority. Wirtschaftspark 27, 9492 Eschen, Liechtenstein.
- Stolen Device Protection: How the new iOS 17.3 feature keeps your iPhone safer - "The new feature in iOS 17.3 aims to make it harder for thieves to mess up your digital life using a stolen passcode. The basic idea is simple: with Stolen Device Protection activated, your iPhone will require biometric identification (Face ID or Touch ID) to perform many actions - your iPhone passcode will no longer serve as a fallback for most of them."
- STOOF INTERNATIONAL - international manufacturer of armoured and specialty vehicles. Offers after-sales support and security driver training. Based in Germany.
- Stop using Alexa & Google Assistant while working until you change these settings - "When people work form home, the line between their professional and personal lives doesn’t just blur, it often gets erased. That means personal privacy concerns become company security concerns. Thus, asking Alexa to make you an espresso while on a Zoom call seems innocent enough. But if the device captures sensitive, work-related information (and can easily be hacked), it could create a nightmare scenario for your company’s IT security team."
- Strava app: Location of world leaders including Putin, Trump & Macron revealed by bodyguards' Strava app - "The French presidential office has now told security agents to not use the fitness app. Some of the world’s most prominent leaders’ movements were tracked online through a fitness app used by their bodyguards, an investigation has suggested."
- STUN GUN
- Surfshark VPN - since 2018. "Secure Your Digital Life with an award-winning VPN." Improve your online security & privacy with a VPN. Take it to new heights with Surfshark. Install Surfshark VPN today and enjoy a premium experience for a friendly price. 3200+ servers worldwide. 24/7 support. RAM-only servers. Audited: No-logs VPN. Unlimited devices.
A
B
C
D
E
F
G
H
I
J
K
L
M
N
O
P
Q
R
S
T
U
V
W
X
Y
Z
- T -
- Tails - "Privacy for anyone anywhere." Live operating system, that you can start on almost any computer from a DVD, USB stick, or SD card. It aims at preserving your privacy and anonymity, and helps you to: use the Internet anonymously and circumvent censorship; all connections to the Internet are forced to go through the Tor network; leave no trace on the computer you are using unless you ask it explicitly; use state-of-the-art cryptographic tools to encrypt your files, emails and instant messaging.
 - TASER - "The Safest, Most Effective Options for Personal Protection for You and Your Family."
- Telegram: 'The dark web in your pocket' - "'There is no doubt that criminality is happening on other social networks too, but my experiment hints at a broader problem that many in law enforcement have been concerned about for years. Here is a flavour of some of the groups to which I have found myself added.'"
  - Terrapin Technology - "The Terrapin Technology Briefcase in cognac is made from genuine Italian leather. It contains Honeywell Spectra Shield within the back face and the flap, giving an excellent surface area of protection from 9mm bullets, knives and shrapnel."
- 'Test your security skills with our nightmare password generator' - The Verge.
- The best outdoor security camera - "Use this to spot animals at night (and package thieves during the day)."
- The bunker builders preparing for doomsday - "For some, the current crisis is a dummy run for long-term lockdown. Across the world, luxury bunkers are being built for a lucky few to survive calamity and collapse."
- The cheap security cameras inviting hackers into your home - "More than 50,000 internet-connected cameras being sold at Amazon and other retailers could have critical security flaws putting consumers’ privacy at risk."
- The companies that help people vanish - "Each year, some choose to 'disappear' and abandon their lives, jobs, homes and families. In Japan, there are companies that can help those looking to escape into thin air."
- The doomsday bunker market is thriving amid the coronavirus pandemic - "Home, sweet, home? COVID-19 is fueling a boom in the doomsday bunker market, thanks to some dubious marketing claims."
- The online data that's being deleted - "For years, we were encouraged to store our data online. But it's become increasingly clear that this won't last forever - and now the race is on to stop our memories being deleted."
- The state of cyber security: we’re all screwed - The Guardian.
- THE STRONGBOX PASSWORD SECURITY SYSTEM - website security: cryptographically secure site defense system.
- The Wired Guide to Your Personal Data (and Who Is Using It) - Wired.
- Think your iPhone is safe from hackers? That’s what they want you to think ... - "Forget Apple’s much-vaunted iOS safeguards - attackers have been quietly breaking and entering for years."
- This Sleek 311-Foot Megayacht Concept Is a Floating Fortress- "With a Safe Room and Counter-Intelligence Protocols. There's even a diplomatic-grade secure meeting room for your classified convos."
- Top Secret Museum - Oberhausen, Germany. "The World's Most Comprehensive Exhibit On Espionage."
- Tor - since 2002. "Browse Privately. Explore Freely." Defend yourself against tracking and surveillance. Circumvent censorship. Tor Browser isolates each website you visit so third-party trackers and ads can't follow you. Any cookies automatically clear when you're done browsing. So will your browsing history.
- Tor’s shadowy reputation will only end if we all use it - "It's not the criminal hacking browser you think it is."
- TRAVEL RISK MAP 2016 - Global health & travel security risks review.
- Travel Tips for Seeing the World’s Best Places - "From fake wedding bands to decoy wallets, here's some advice for safely roaming our planet."
- Turn an Obsolete Phone Into a Free Security Camera With 3 Easy Steps - "If you're replacing your iPhone or Android phone, we've got the perfect idea for your old model: Turn it into a free home security camera with the right app."
- Turn off your Bluetooth, warn security experts - "Your Bluetooth connection is unsafe. Very unsafe. That’s the message from the largest hacker convention."
- Turn off your iPhone for five minutes - cybersecurity advice - "Forcibly closing apps could stop criminals from monitoring users or collecting data."
- TWO WAY MIRROR - custom cut to the size you need.
- Tychem - "Protecting Industrial Workers for 30 Years." Not all deadly threats come in the form of guns or other weapons. For protection against chemical dangers, industrial workers rely on DuPont Tychem garments.
- Typing these four characters could crash your iPhone - "A newly discovered bug causes iPhones and iPads to briefly crash. All you need to trigger the bug are just four characters."
A
B
C
D
E
F
G
H
I
J
K
L
M
N
O
P
Q
R
S
T
U
V
W
X
Y
Z
- U -
- UNDERGROUND VAULTS & STORAGE - specializes in secure records and asset storage and management. UV&S serves national and international clients representing numerous industries including healthcare, legal, financial, insurance, cultural, oil/gas, entertainment, and government.
- UNIVERSAL HANDCUFF KEY - plastic handcuff key. Undetectable by metal detectors. Opens all cuffs.
- U.S. TRAINING CENTER - training today to meet the challenges tomorrow.
- US warns hundreds of millions of devices at risk from newly revealed software vulnerability - "Hundreds of millions of devices around the world could be exposed to a newly revealed software vulnerability, as a senior Biden administration cyber official warned executives from major US industries Monday that they need to take action to address 'one of the most serious' flaws she has seen in her career."
- Use iOS 15's Built-in Authenticator as a Secure 2FA Method for All Your Accounts - "Most websites and apps support two-factor authentication (2FA), which adds an extra layer of security to your accounts by requesting another form of identification beyond username and password. The second factor can be a recovery code, physical security key, or one-time password (OTP) that only you can access, even if someone else has your password. This process is easier than ever thanks to iOS 15."
- UZI - the official UZI website.
A
B
C
D
E
F
G
H
I
J
K
L
M
N
O
P
Q
R
S
T
U
V
W
X
Y
Z
- V -
 - Vampire Straw - "Machined one at the time in the USA out of grade 9 titanium, the Vampire straw is truly a custom made item. The Vampire straw’s dimensions make it the most comfortable straw to use; it’s length and wide gauge allows the user to drink effortlessly any thick shake or smoothie. The Vampire straw is also long enough to drink from any long beverage can. Designed for self defense, the Vampire straw is super tough and long enough to be used like a dagger; it’s chiseled tip is sharp enough to puncture most synthetic materials. The Vampire straw is also a very effective tire deflator, and can be carried in a cup, in public without attracting attention. From a cup, the Vampire straw is very easy to deploy in reverse grip, and put into action almost instantly."
- vampire straw? A closer look at the weapon confiscated from a Boston traveler’s luggage - "A man was arrested earlier this month at Boston Logan International Airport for allegedly carrying a 'vampire straw' in his carry-on luggage. While the name of the device summons thoughts of Dracula and blood-sucking bats, the straws actually have nothing to do with vampires. Here’s what you need to know about the multi-use, self-defense tool."
- VERISIGN - SSL certificates, and more.
- Verizon VPN app protects against shady public WiFi - "It can also block ad trackers."
- VIP BODY ARMOR - "The premier provider in bulletproof fashion, VIP Body Armor / VIP Body Armor designs bulletproof clothing that embodies fashion with security."
- VPN Guide: Legality, Jurisdictions & Internet Censorship - since 2012. "The Best VPN Reviews on Earth!"
- VPNPro.com - "Your Roadmap To Online Privacy And VPN Technology." Here at VPNpro, we keep a close eye on the ever-changing World Wide Web and give you the latest on online safety and the VPN industry.
- VPN Services Resources - reviews, guide & tips.
A
B
C
D
E
F
G
H
I
J
K
L
M
N
O
P
Q
R
S
T
U
V
W
X
Y
Z
- W -
- Wayback Machine internet archive - since 1996. "As of February 2021, the Internet Archive holds over 29 million books and texts, 8.7 million movies, videos and TV shows, 629,000 software programs, 16 million audio files, 3.8 million images, 224,000 audio files, and 550 billion web pages in the Wayback Machine."
- what Amazon knows about you & how to stop it - "The tech giant has many ways of gathering information about its users’ activity - from Prime to Alexa. But how much can it collect and what can you do to keep your life private?"
- What is Pegasus spyware & how does it hack phones? - "NSO Group software can record your calls, copy your messages and secretly film you."
- What really happens to your phone when it’s stolen - "The racket fuelling organised crime is evolving beyond snatchers on bikes - and the Met police commissioner says Apple and Google could stop it if they wanted to."
- What the Bible Says About Secrets - "Scripture offers at least two views of privacy: It’s necessary for a healthy spiritual life, but it also provides a place where sin can be committed."
- WhatsApp Backlash - Stop Using Signal Or Telegram Until You Change These 4 Critical Settings - "Telegram and Signal continue to surge following WhatsApp’s privacy backlash—tens of millions of you are now using these messengers for the first time. But, just like WhatsApp, Telegram and Signal have critical settings you must change before you start using the apps. Here’s what you need to do now."
- WhatsApp Discovered Malware That Infects Phones With a Missed Call - "Spyware crafted by an 'advanced cyber actor,' reportedly an Israeli company, infected multiple targeted mobile phones through WhatsApp's in-app voice calls."
- Who listens in on a president's phone call? - "A whistleblower's complaint alleging that records of a call made by President Donald Trump was handled in an unusually secretive way has shone a spotlight on how such calls are monitored - and how they can be hidden."
- Who’s behind the Kaseya ransomware attack & why is it so dangerous? - "The breach has affected hundreds of businesses around the world, and experts fear the worst is yet to come."
- Why Amazon knows so much about you - "How Jeff Bezos built his data machine."
- Why Apple’s walled garden is no match for Pegasus spyware - "Pegasus can infect a phone through ‘zero-click’ attacks, which do not require any interaction from the phone’s owner to succeed."
- Why are billionaires like Mark Zuckerberg building bunkers & buying islands? - "Tycoons who buy underground bunkers may seem like they’re preparing for apocalypse - but they’re not, say these University of Queensland researchers."
- Why do I have to take my laptop out of the bag at airport security? - "The main reason you have to remove your laptop from your bag is because its battery and other mechanical components are too dense for X-rays to penetrate effectively - especially if the scanning system is old. The same goes for power cords and other devices such as tablets and cameras."
- Why I turned on iMessage "Encrypted chat is a moral imperative."
- Why phones that secretly listen to us are a myth - "A mobile security company has carried out a research investigation to address the popular conspiracy theory that tech giants are listening to conversations."
- Why you need a VPN for surfing on public Wi-Fi - "Public Wi-Fi connections are dangerous if you don’t have any security measures in place. Your data is at risk. Here’s how to protect it."
- Why You Should Never Borrow Someone Else's Charging Cable - "Protect your charging cables like you protect your passwords, say cybersecurity experts."
- Why You Should Never Use Google Chrome On Your iPhone, iPad Or Mac - "Chrome has been under fire for its 'creepy' new tracking technology for some time, but now we have a more detailed technical analysis of the very serious risks to users and an update from Apple that highlights exactly why Chrome is such a privacy nightmare. Apple users should certainly not be using Chrome on any of their devices."
- Why You Should Stop Sending SMS Messages - Even On Apple iMessage - "Last month, I advised users to stop using Facebook Messenger and switch to its stablemate WhatsApp. The reason is simple - security. This led to people asking me about Apple iMessage and SMS - including Google Messages, and whether these are secure to use. The answer is not as simple as you might like."
- Why You Should Stop This ‘Dangerous’ Update To Your Amazon Account - "Cybersecurity experts are warning Amazon customers to beware a new account update being rolled out to the company’s smart devices installed in millions of homes. The plan is for those customers to share their home broadband with neighbors, to make their devices work more effectively and over longer distances. This new account setting will be on by default, impacting many Echo and Ring devices - you actually need to log into your account to switch it off."
- Why You Should Stop Using This ‘Dangerous’ WhatsApp Setting On Your iPhone - "When you come to move your WhatsApp account from your old device to your new one, you’ll be directed to use WhatsApp’s iCloud backup option to transfer your message history, media and settings. But those backups are not protected by WhatsApp’s end-to-end encryption. It’s a serious privacy and security vulnerability - one that rivals iMessage and Signal have resolved."
- Why You Suddenly Need To Delete Gmail On Your iPhone - "Gmail has already come under attack for its alarming privacy labels. But a new update from Apple, combined with a privacy backlash this month against 'creepy' mail tracking, should now be the final convincer for millions of users to delete their Gmail apps, ensuring that their data is not being secretly harvested."
- WISEKEY - founded in 1999. Provides specialized security and digital identification cutting edge technologies for personal data protection, effective identification and authentication of people and objects.
 - Withings Home - "Security is a beautiful thing." Be home from anywhere. With its ability to stream HD video and facilitate family interactions, the Withings Home is the most comprehensive house monitoring solution. Home works with your smartphone, your tablet, your Apple watch and is the first camera you can stream on your Apple TV.
- World Backup Day - March 31st - "Be prepared against data loss and data theft. March 31st is the day to backup and better protect your data."
- 'world's safest city' for 2021 revealed - "Safety has long been a paramount concern for travelers when it comes to deciding which destination to visit. But the world has been turned on its head in recent years due to the global pandemic and the notion of exactly what makes somewhere 'safe' has changed significantly. This may help to explain the shake up at the top of the Economist Intelligence Unit's Safe Cities Index (SCI,) which ranks 60 international destinations on digital security, health security, infrastructure, personal security, as well as environmental security, a new category for this year. Copenhagen has been named the world's safest city for the first time, scoring 82.4 points out of 100 in the annual report."
A
B
C
D
E
F
G
H
I
J
K
L
M
N
O
P
Q
R
S
T
U
V
W
X
Y
Z
- X -
- XE SERVICES LLC - "Where excellence is the standard." Still usually referred to as "Blackwater", is a private military security company founded as Blackwater USA in 1997.
A
B
C
D
E
F
G
H
I
J
K
L
M
N
O
P
Q
R
S
T
U
V
W
X
Y
Z
- Y -
- You Can Still Use WhatsApp - But Change These 3 Critical Settings First - "If you’re a WhatsApp user, you will have seen the alarming stories warning about the messaging platform’s surprise privacy changes, many suggesting you switch to alternatives. The good news is you don’t need to do that - WhatsApp is still okay to use. The bad news, though, is that you do need to change these critical setting to stay safe."
- You should change these Roku, Apple TV, Fire TV & Chromecast privacy settings now - "It can be hard to find the privacy settings on your streaming devices. Here's how to make sure your viewing habits aren't being tracked."
- You Should Stop Using Texts for Two-Factor Authentication - Wired.
- You think you’re watching smart TV ... In fact it’s watching you - "Tech giants hoover up data not just on viewing but on purchasing habits and may even have a back door into your emails - and they don’t make it easy to opt out. At the heart of this is a technology called 'automatic content recognition' (ACR) which is constantly taking snapshots from your TV screen."
- Your battery status is being used to track you online - The Guardian.
- Your car knows secrets about you. Here's how to protect yourself - "Cars increasingly resemble a smartphone on wheels, storing personal information such as our location, how we drive, who we talk to and how to reach them. Some even hold a way to join our home WiFi network. If you've ever sold an old smartphone or laptop, you probably thought to wipe the hard drive first, to protect your privacy. When we sell a car, or return a rental car, a similar thought may not cross our minds, but cybersecurity experts say it should."
- Your mobile phone is listening to your conversations - but now you can stop the snooping - "Ever feel like your phone has been eavesdropping on your conversation? Those ads which suddenly appear on your feeds after you were discussing the products are far from a quirky coincidence."
- Your 'private' Instagram account isn't as private as you think - "Your followers can still share and save your posts without your knowledge by using a surprisingly simple trick."
- Your Wi-Fi Security Is Probably Weak. Here’s How to Fix That - The New York Times.
 - YubiKey NEO - "NFC Security Key." In a single device, the YubiKey NEO has both contact (USB) and contactless (NFC, MIFARE) communications. It supports one-time password, smart card functionality, including OpenPGP and PIV, and the emerging FIDO Alliance Universal 2nd Factor (U2F) protocol. Takes two-factor authentication to the next level. Use it along with a username and password to prove your identity and prevent hackers from breaking into your accounts. It’s specially designed to fit on a keychain, which means it goes wherever they (and their car keys) go." - (Wired.)
A
B
C
D
E
F
G
H
I
J
K
L
M
N
O
P
Q
R
S
T
U
V
W
X
Y
Z
- Z -
- Zoom paid accounts reportedly will get strong encryption for calls - "End-to-end encryption won’t be coming to all customers’ video calls, however."
|
|














































