200 Physical & Virtual Security Resources & Suppliers
SECURITY is the degree of protection against danger, loss, and criminals. Security has to be compared and contrasted with other related concepts: Safety, continuity, reliability. The key difference between security and reliability is that security must take into account the actions of people attempting to cause destruction.
Security as a state or condition is resistance to harm. Security as a form of protection are structures and processes that provide or improve security as a condition. Security is also defined as "a form of protection where a separation is created between the assets and the threat. This includes but is not limited to the elimination of either the asset or the threat. In order to be secure, either the asset is physically removed from the threat or the threat is physically removed from the asset.
PHYSICAL SECURITY describes both measures that prevent or deter attackers from accessing a facility, resource, or information stored on physical media and guidance on how to design structures to resist various hostile acts. It can be as simple as a locked door or as elaborate as multiple layers of armed Security guards and Guardhouse placement. Physical security, by no means, is a modern phenomenon. Physical security, as a field, exists in order to deter persons from entering a physical facility. Thus, as long as the need to defend physical facilities has existed, a need to provide for their security has also been needed. Historical examples of physical security include city walls, moats, booby traps, etc. The key factor is the technology used for physical security has changed over time. While in past eras, there was no Passive Infrared (PIR) based technology, electronic access control systems, or Video Surveillance System (VSS) cameras, the essentially methodology of physical security has not altered over time.
INTERNET SECURITY: When a computer connects to a network and begins communicating with others, it is taking a risk. Internet security involves the protection of a computer's internet account and files from intrusion of an unknown user. Basic security measures involve protection by well selected passwords, change of file permissions and back up of computer's data.
Anonymity | Encryption
 - 7 benefits of using a VPN (spoiler: it could save you money) - "We all regularly use the internet nowadays for a variety of different purposes. Whether it’s to keep in touch with friends and family, to work from home, or to conduct our banking and bill paying online, it’s important to be secure. One of the best ways to keep yourself secure and your activity private is to use a VPN."
- 10 BEST VPN SERVICES 2018 - PCMagazine.
- Anonymity application - Wikipedia.
- APP THAT ENCRYPTS YOUR PHOTOS FROM CAMERA TO CLOUD - Wired.
- Apple’s Face ID wipes the floor with Android’s facial recognition - BGR.
- Apple's statement to Congress on the FBI warrant fight - The Verge.
- Atlas VPN Launches Its Free Mobile Service to Protect Security Online - "A new, reliable and free VPN will combat shady players for free VPN market share. All this, while keeping a strict no-logs policy and not pushing ads to its users."
- Building a new Tor that can resist next-generation state surveillance - Tor is an imperfect privacy platform. Ars meets the researchers trying to replace it.
- Don’t use a free VPN - you’ll be putting your data at risk - "With money tight, it’s super tempting to go with a free VPN, right? You really shouldn’t. At least not for long-term use. Sure, some of the best free VPNs could be worth checking out if you’re desperate but for the most part, you really need to sign up to the best VPN that costs money. Once you’ve delved into knowing exactly what a VPN is, it should make a lot of sense why going a paid route is a better option. If you’re still not sure, read on while we break it down for you."
- Eliminalia - "We erase your past we help you build your future." We help you rebuild your future by deleting unwanted and erroneus information and help guarantee your right to anonimity.
- ENCRYPTION - Wikipedia.
- Hashing - transformation of a string of characters into a usually shorter fixed-length value or key that represents the original string.
- How to Protect Your Smart Home From Hackers - "Smart home devices can make life more convenient, but may put you at risk of being hacked. Ensure your safety with a few simple measures."
- Onion routing - Wikipedia.
- Playing Dead: Journey Through World of Death Fraud - "How the Philippines became the global leader for a macabre trade."
- ONLINE ANONYMITY - Wikipedia.
- Playing Dead: Journey Through World of Death Fraud - The Telegraph.
- Privacy mode - can be enabled so that the browser does not store this information for selected browsing sessions. Privacy mode will also disable the storage of data in cookies and Flash cookies.
- The Privacy Surgeon - "Dissecting the issues that matter to you."
- True Private Messaging - 7 Apps to Encrypt Your Chats.
- VIRTUAL PRIVATE NETWORK | VPN - private network across public networks like the Internet.
- VPN Beginner’s Guide - "What is a VPN and how does it work (Explained)."
- VPN Guide: Legality, Jurisdictions & Internet Censorship - since 2012. "The Best VPN Reviews on Earth!"
- 4chan - since 2003. English-language imageboard website. Users generally post anonymously, with the most recent posts appearing above the rest. 4chan is split into various boards with their own specific content and guidelines. Registration is not required, nor is it possible (except for staff).
- ANONYMIZER - email & Internet anonymity.
- Atlas VPN - "Fastest Free VPN Service." Atlas VPN is a free VPN app that ensures private browsing by changing your IP address and encrypting your connections.
- FAKE NAME GENERATOR - "Generate a Random Name." The most advanced name generator. With 30 languages and 22 countries, the Fake Name Generator is the most advanced name generator on the internet.
- Ghostmail - "Secure & Private Encrypted Email." Sign up to military grade encrypted GhostMail and enjoy instant free and secure email & chat. No download or installs needed.
- GOOGLE ANALYTICS OPT-OUT BROWSER ADD-ON - provide website visitors more choice on how their data is collected by Google Analytics.
- GOOGLE SHARING - how to hide from Google. A special kind of anonymizing proxy service, designed for a very specific threat. It ultimately aims to provide a level of anonymity that will prevent google from tracking your searches, movements, and what websites you visit.
- HIDE MY ASS - "VPN client software. VPN connections made easy." Securing and encrypting your internet connection has never been so easy. Simply install our software, enter your username and password and click the connect button! Absolutely no technical knowledge is required.
- Hotspot Shield - since 2005. "Free VPN Service." Allows users to surf the Internet privately by creating a virtual private network so the user can gain secure access to all internet content, while staying in control over their personal privacy.
- How to secure your phone before attending a protest - "If you’re attending or even just watching the protests, then be aware: not only is your phone a trove of information about you and the people you communicate with, but it also functions as a tracking device. That’s why it’s important to keep your digital footprint as small as possible - any evidence placing people at protests could be enough to get them arrested. You should account for the fact that your phone may get lost, stolen, or broken. There’s also a risk of your phone being confiscated by authorities - which means that if they’re able to unlock your phone, they’ll have access to data on you and people you know. In other words, it never hurts to prepare for the worst, especially considering recent events. The steps we’ve listed here are a basic start toward protecting your privacy before you attend a protest."
- How to set up two-factor authentication on all your online accounts - "An extra step of security never hurt anybody."
- HTTPS Everywhere - Firefox and Chrome extension that encrypts your communications with many major websites, making your browsing more secure.
 - I2P - "The Invisible Internet Project." Since 2003. Computer network layer that allows applications to send messages to each other pseudonymously and securely. Uses include anonymous web surfing, chatting, blogging and file transfers. The software that implements this layer is called an I2P router and a computer running I2P is called an I2P node. The software is free and open source and is published under multiple licenses.
- iMessage - instant messenger service developed by Apple Inc. for iOS and OS X Mountain Lion. Not to be confused with Messages (application). iMessage allows users to send texts, documents, photos, videos, contact information, and group messages over Wi-Fi, 3G or LTE to other iOS or OS X users, thus providing an alternative to standard SMS/MMS messaging for all users with devices running iOS 5 or later. On iPhones, green buttons and text bubbles indicate SMS-based communication; on all iOS devices, blue buttons and text bubbles indicate iMessage communication. All iMessages are ENCRYPTED and can be tracked using delivery receipts. If the recipient enables Read Receipts, the sender will be able to see that the recipient has read the message. iMessage also allows users to set up chats with more than two people - a "group chat".
- Neomailbox - "Secure Email Hosting. Anonymous Surfing. Encrypted Email Service. Offshore Email Accounts." To protect yourself, your family and your organization from the serious and growing risks of profiling, identity theft and privacy invasion online you need strong security for your email and web surfing. Neomailbox has been providing secure and reliable email and private surfing services for over 11 years, enabling thousands of individuals and organizations to protect their privacy online.
- NordVPN - VPN Service since 2008. "A Virtual Private Network (VPN) is a way to conceal your activity online. When you use a VPN your data connection is encrypted, meaning that others (such as your Internet Service Provider) cannot see which websites you visit, what you download or whether you use websites such as Skype or bit torrent applications. NordVPN works at the TCP/IP level, which means that all of your applications will be secured and protected, not just your web browser. And because we’ve designed the NordVPN service to work instantly with the technology already installed on your computer and smartphone, you can enjoy the benefits of your own Virtual Private Network in minutes, for less than a penny (Euro cent) per day."
- Off-the-Record Messaging - allows you to have private conversations over instant messaging by providing: Encryption (No one else can read your instant messages), Authentication (you are assured the correspondent is who you think it is), Deniability (the messages you send do not have digital signatures that are checkable by a third party), Perfect forward secrecy (if you lose control of your private keys, no previous conversation is compromised).
- PGP | PRETTY GOOD PRIVACY - since 1991. Data encryption and decryption computer program that provides cryptographic privacy and authentication for data communication. PGP is often used for signing, encrypting, and decrypting texts, e-mails, files, directories, and whole disk partitions and to increase the security of e-mail communications.
- Proof of Existence - Provides Intellectual Property Rights. Can be used to demonstrate document ownership without revealing the information it contains, and to provide proof that a document was authored at a particular time. The key advantages are anonymity, privacy, and getting a decentralized proof which can't be erased or modified by anyone (third parties or governments).
- PSIPHON - "Uncensored Internet access for Windows and Mobile." Develops a wide range of tools and solutions aimed at preserving security, privacy, and access to content.
- Secure Drop - open-source whistleblower submission system managed by Freedom of the Press Foundation that media organizations use to securely accept documents from anonymous sources.
- Surfshark VPN - since 2018. "Secure Your Digital Life with an award-winning VPN." Improve your online security & privacy with a VPN. Take it to new heights with Surfshark. Install Surfshark VPN today and enjoy a premium experience for a friendly price. 3200+ servers worldwide. 24/7 support. RAM-only servers. Audited: No-logs VPN. Unlimited devices.
- Tails - "Privacy for anyone anywhere." Live operating system, that you can start on almost any computer from a DVD, USB stick, or SD card. It aims at preserving your privacy and anonymity, and helps you to: use the Internet anonymously and circumvent censorship; all connections to the Internet are forced to go through the Tor network; leave no trace on the computer you are using unless you ask it explicitly; use state-of-the-art cryptographic tools to encrypt your files, emails and instant messaging.
 - Tor | The Onion Router - since 2002. "Browse Privately. Explore Freely. Defend yourself against tracking and surveillance. Circumvent censorship." System intended to enable online anonymity. Tor client software directs internet traffic through a worldwide volunteer network of servers to conceal a user's location or usage from anyone conducting network surveillance or traffic analysis. Using Tor makes it more difficult to trace Internet activity, including "visits to Web sites, online posts, instant messages and other communication forms", back to the user and is intended to protect users' personal freedom, privacy, and ability to conduct confidential business by keeping their internet activities from being monitored.
- TorGuard - "Online privacy protection services." Anonymous VPN Service: Anonymize and Encrypt all web Traffic through Private VPN Service. Anonymous Proxy: Keep Your Personal Identity Anonymous & Private on Bittorrent. Stealth VPN: Bypass DPI Firewalls and VPN Blocks with TorGuard Stealth VPN. Private Email: Communicate in Complete Security with OpenPGP email Encryption.
- Tox - "A New Kind of Instant Messaging." Free and open-source, peer-to-peer, encrypted instant messaging and video calling software. With the rise of government monitoring programs, Tox provides an easy to use application that allows you to connect with friends and family without anyone else listening in. While other big-name services require you to pay for features, Tox is totally free, and comes without advertising.
- TRUECRYPT - "Free Open-Source On-The-Fly Encryption." TrueCrypt is free open-source disk encryption software for Windows 7/Vista/XP,
Mac OS X and Linux. In case an attacker forces you to reveal the password, TrueCrypt provides and supports two kinds of plausible deniability.
- Unblock-US - "Smart faster VPN." Unblock your freedom. Bypass blocks and protect your identity online. Every computer or other Internet-enabled device has an address. It's made up of numbers, like a street address. Our solution is brilliantly simple. We give you an address where the content you want is available. It's like moving your computer or other device without actually moving it.
Armored Vehicles
 - 10 Most Expensive Armoured Vehicles In The World - TheRichest.
- AL CAPONE'S ARMORED 1928 CADILLAC - Federal Times.com
- AL CAPONE'S ARMORED 1930 CADILLAC
- ARMORED CAR (VIP) - Wikipedia.
 - Dillon Aero Convoy Escort Vehicle (CEV) - DillonAero.
- Donald Trump's presidential armored car is almost ready - Daily Mail.
- OFFICIAL STATE CAR - Wikipedia.
 - Presidential state car (United States) - (nicknamed "The Beast", "Cadillac One", "Limousine One", "First Car"; code named "Stagecoach") is the official state car of the President of the United States.
- PROTECTION LEVELS - B1-B6.
- alpha armouring - "Armored Cars, SUVs made in Germany."
- Alpine Armoring - "Armored Vehicles & Armored Cars."
- ARMORTECH - Russian international manufacturer and provider of armoured and specialty vehicles.
- AUDI A8 L SECURITY W12 - combines outstanding protection with unique safety features to produce a convincing all-round safety package.
- BLINDCORP - all bulletproofing processes are conducted in accordance with the regulations established by car manufacturers such as Mercedes Benz, BMW, Audi and Lexus, among others.
- BMW 7 SERIES HIGH SECURITY - BMW is the first manufacturer to offer a car that is fully compliant with the requirements of the class VR7 ballistic protection standard.
- BMW SECURITY VEHICLES
- CENTIGON - security vehicles, armored cars, special limousines. World's largest armored vehicle manufacturer and global security systems provider.
- CJL Armoured Protection vehicles - "Armoured & Luxury Chauffeur Driven Cars." Discreet Professional Protection.
- CONQUEST VEHICLES - ultra-luxurious, fully armored, handcrafted sport utility vehicles.
- IAG | INTERNATIONAL ARMORED GROUP - based in U.A.E. "Premium manufacturer of custom armored vehicles with over 17 years of experience. We have built and sold thousands of armored vehicles to organizations such as the US government/military, United Nations, NATO, embassies and private security companies as well as various individual clients worldwide."
- JANTI SECURITY SERVICES - "Quality Service beyond Excellence." Sales, distribution, building of fleets, and maintenance of new armored vehicles, bullet proof cars, buses, and SUVs which are approved by "NIJ" National Institute of Justice, which has approved Armoring levels B4 to B7.
- MAYBACH GUARD - a high level of protection encapsulated in luxurious curves.
- Mercedes-Benz S600 Pullman Guard - (2010-). Armoured, prestige limousine with integrated highest protection.
- RIDA - on stock. Reliable protection and best prices.
- STOOF INTERNATIONAL - international manufacturer of armoured and specialty vehicles. Offers after-sales support and security driver training. Based in Germany.
- The Armored Group | TAG - since 1992. Bullet proof automobiles, trucks, and vehicles.
Bodyguard Services
 - Academi - previously known as Xe Services LLC, Blackwater USA and BLACKWATER Worldwide - is a private military company founded in 1997. Currently the largest of the U.S. State Department's three private security contractors.
- ARMOR GROUP - the world's leading security solutions group.
- AS SOLUTION - Customized International Protection & Security. "We Customize Our Services to Support Our Client’s Lifestyle."
- BODYGUARD - Wikipedia.
- celebrity bodyguards tell their stories - The Guardian.
- HART SECURITY - "When You Face Risk, You Need Hart." An internationally recognized risk management company, Hart delivers innovative, integrated security solutions in complex areas across land, sea and air.
- How to Hire a Bodyguard - wikiHow to do anything.
- How to Understand the Structure of a Simple Non Disclosure Agreement - wikiHow to do anything.
- SOLDIER OF FORTUNE MAGAZINE - motto of the magazine is "The Journal of Professional Adventurers."
- The 10 Most Famous Bodyguards Of All Time - TheRichest.
- Top Body Guard Services Companies in Security - SecureTech.
Dubai, U.A.E.
- HART SECURITY - since 1999. "When You Face Risk, You Need Hart." An internationally recognized risk management company, Hart delivers innovative, integrated security solutions in complex areas across land, sea and air.
Sweden
- Private Bodybuard Service | PBS founded in 1999 by Moore Jonson, who has many years of professional training with an edge in protection. Today, PBS is one of the most respected body guard services around the world; much due to the unique training our employees exercise regularly.
Ukraine
- TopGuard Security - "Security Company Ukraine Kiev Armed Guards Bodyguards Security Services." TopGuard is a leading company in the Ukrainian market of security services. Our experience helps us to provide maximum quality of security services, in accordance with European norms and standards. All our bodyguards take special education and training and they are reayd to any non-standard tasks and situations.
United Kingdom
- ARMOR GROUP - British company providing private security. It was founded in 1981 and was listed on the London Stock Exchange until 6 June 2008 (it was acquired by G4S plc in April 2008).
- Croma Security Solutions - "Croma Vigilant provides keyholding, security guards and mobile patrols as well as more specialist security services throughout the UK. We are run by ex-military personnel and military standards are embedded in the DNA of the company."
- G4S - "Security Services and Systems." The secure solutions businesses provides a broad range of solutions to both commercial and government customers.
- HART SECURITY - "When You Face Risk, You Need Hart." An internationally recognized risk management company, Hart delivers innovative, integrated security solutions in complex areas across land, sea and air.
- ICP | International Corporate Protection - "Threat Management Services. Personal Security & Protection. Corporate Security. Corporate Training. Intelligence Services. Hi-Tech Security."
- LONGMOOR GROUP - "Longmoor Security are specialists in providing world class Close Protection and protective security solutions that provide peace of mind to our clients allowing them to function in the areas they would not normally operate."
- LOOMIS - "Managing Cash in Society." Loomis has an illustrious heritage and a long history of managing cash. We have a strong international presence with about 400 branch offices spread across more than 20 countries.
- Paradigm Security Solutions - "Level 3 Close Protection Training."
- The Panic Room Company - "A new concept in personal protection." Our Panic/safe room has been developed from over 2 decades protecting staff and assets across the United Kingdom. Our Safe Room has passed various Ballistic tests that allow it to protect individuals in even the most hostile situations. Due to its unique modular design, our Safe Room can be installed quickly with little disruption into most buildings.
- Umbra - "UMBRA is the only company providing elite, highly trained female Security professionals globally."
- Virtus Risk Management - since 2011. "Leading Security and Investigations Company." Manage your risk with specialist investigation services and security consultancy provided by experienced professionals.
U. S. A.
- Academi - previously known as Xe Services LLC, Blackwater USA and BLACKWATER Worldwide - is a private military company founded in 1997. Currently the largest of the U.S. State Department's three private security contractors.
- Beau Dietl & Associates - since 1985. "Our Escort Protective Services team applies their previous law enforcement experience to personal protection. They accompany the subject whenever or wherever needed."
- Blackwater Protection - "The top security service provider in Miami and the surrounding cities. We offer private security services for events, corporate events, condos, & construction. Our security company provides clients many options when selecting the service mix right for the property, personnel, and other assets they wish to protect. Also our security professionals have the expertise to develop solutions that effectively maximize service levels for each client needs."
- BRINK'S - since 1859. "Secure Transportation, Cash Handling, Security Services." Global leader in security-related services for banks, retailers and a variety of other commercial and governmental customers in more than 100 countries.
- Cass Global - "CASS GLOBAL is a US corporation with nearly three decades of experience in International Executive Protection and Crisis Management."
- Celebrity Bodyguard Services - "We specialize in Bodyguard Services for high profile celebrities of film & television, the music industry, and professional sports entertainment. With Private Executive Protection agents in 32 cities, our team can provide you and your clients with excellent service at a competitive price."
- ETS - Global Risk Management - "Celebrity Bodybuard Security Services & VIP Protection Company." ETS understand that certain celebrities and people in the media spotlight may require bodyguard services for short durations when traveling to special events or media appearances. Whether a celebrity traveling to NYC to record a tv show, or a celebrity appearing at a Red Carpet event - ETS are able to provide highly experienced personal bodyguards and security personnel.
- Fast Guard Service - "#1 VIP Bodyguard Protection & Private Security Consultants." Emergency Response Security On Site within 4 hours or less.
- Guardian Protection Force - "We are a Northern California Private Security Company aiming to offer a higher quality security service than our competitors. We offer security solutions from consulting, to executive protection, as well as armed and unarmed officers." Furthermore, Guardian is able to conduct operations worldwide.
- K2 Intelligence - since 2009. "An industry-leading investigative, compliance, and cyber defense services firm with a reputation for investigative, analytic, and advisory excellence."
- Kroll - "We expertly address physical security and operational risk issues by employing a holistic approach, encompassing all aspects of a client’s operations."
- PINKERTON - since 1850. "VIP and Celebrity Bodyguard Services." Pinkerton offers national and global organizations a vast selection of reliable risk management services and solutions, including: Investigations; Protective Services; Crisis Management & Emergency Services; Employment Screening; Security Management & Consulting; Intelligence & Information Services; and Brand Protection & Intellectual Property.
- Security USA - "The Ultimate Secutiry Solutions." Our New York Security and Bodyguard company is located in Midtown Manhattan, NYC and we specialize in the field of security, both in the personal and business security sectors. Our clients know us for our bodyguards our outstanding security services, our diverse security solutions, and for the pride we take in our work.
- VIP protective services - "The new standard in security." Professional Security Guard & Patrol Service serving the rntire Bay Area.
Bulletproof Clothing
 - 10 COOLEST BULLETPROOF THINGS YOU CAN BUY TODAY - Thrillist.
- America Has a Growing Demand for Bulletproof Clothing - BodyArmorNews.com.
- Ballistic Resistance of Body Armor NIJ Standard - National Institute of Justice.
- Body armor - Wikipedia.
- BODY ARMOR NEWS - "Specialized in providing news and updates on bullet proof vests."
- Bulletproof Fashion for Men: Extreme Clothing for the World Traveler - Forbes
- Bulletproof Style: Menswear Company Creates Ballistic Suits, Shirts & Even Underwear - TheBlaze.
- Bulletproof vest - Wikipedia.
- Bulletproofing - Wikipedia.
- History of Body Armor and Bullet Proof Vests - ThoughtCo.
- How to look good when you're dodging bullets - The Independent.
- Inside America’s Growing Bulletproof Clothing Industry - Racked.
- John Wick’s Bulletproof Suit - "Are kevlar-lined suits the real deal?"
- Miguel Caballero - bulletproof clothing company based in Bogotá, Colombia, Mexico and Guatemala. It is mostly known for its fashion line of bulletproof clothing and counts among its clients King Felipe VI of Spain, the Former Mayor of New York Michael Bloomberg, the ex-President of Colombia Álvaro Uribe, the ex-President of Venezuela Hugo Chávez, the former President of the United States Barack Obama, the President of Mexico Enrique Peña Nieto and other VIPs.
- NIJ BODY ARMOR STANDARD OVERVIEW - "Provides The Performance Level For Most Ballistic-Resistant Vests."
- Secret Agent Magazine - "Find the latest fashions in anti-ballistic apparel."
- Suit Up With These 3 Pieces of Bulletproof Clothing - Popular Science.
- Style Under Fire: Our Favorite Bulletproof Clothing - GQ.
- The $3.2 Million Bulletproof, Diamond-Studded Suit With a Built-In A/C - Daily Mail.
- The Rise of Bulletproof Fashion – It's No Longer About Safety - U.S. News & World Report.
- This designer clothing line is stylish ... and bulletproof - CNN Tech.
- This Is the Bulletproof Limo of Suits - "Aspetto makes bespoke suits that could literally save your life." Esquire.
- Top 5 indestructible bulletproof clothes - YouTube 2:39.
- Toronto tailor introduces bulletproof three-piece suits - The Globe and Mail.
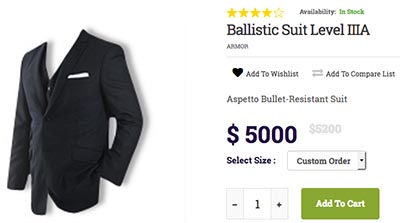 - Aspetto - since 2008. "Subtly Combine Style with Personal Protection." Aspetto is not just concerned with making fine clothing for the ambitious men of the world, but is also serious about your safety. As creator of the lightest, strongest ballistic clothing in the world, Aspetto transforms the luxurious, bespoke Aspetto suits you have come to love into America’s toughest bulletproof suit with IIIA ballistic material.
- BIJAN - since 1976. Bulletproof lined jackets, and much more.
 - BladeRunner - since 2007. "Bullet-Proof Clothing | Ballistic Clothing." Bladerunner stock a wide range of Bullet-Proof Clothing, including ballistic jackets, bullet-proof vests, waistcoats and plates with up to level IV ballistic protection. Our ballistic clothing is ideal for security staff, undercover police, press or simply those who want the reassurance that our bullet-proof clothing provides.
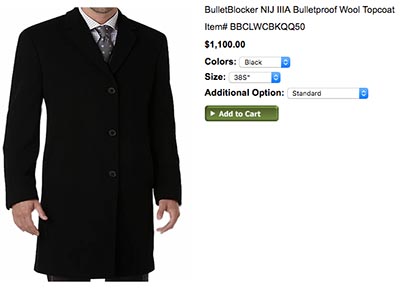 - BULLET BLOCKER - since 2007. "Stylish Bulletproof Clothing." An American company. Prepare. Protect. Prevent.
 - Engarde - since 2003. "A company specializing in state-of-the-art body armor products." Leading manufacturer of high quality body armor used by military, law enforcement and civilian security services around the world. Body armor, helmets, hard armor inserts, bulletproof vests, concealable body armor, tactical body armor, vests, ballistic armor.
 - Garrison Bespoke - since 2008. "Toronto's Best Custom Suit Tailors." Offers bulletproof three-piece suit lined with several ultrathin sheets of carbon nanotube material that can stop a bullet or blade. The suit is built to order and starts at C$20,000.
 - Israel-Catalog.com - "The best Israel has to offer." Lightweight bulletproof flight jacket - level III-A. Designed especially for undercover work: businessmen, detectives, bodyguards, and others to provide maximum ballistic protection.
 - MEN'S BULLETPROOF POLO SHIRT - by Miguel Caballero: US$3,475.00.
 - MIGUEL CABALLERO - since 1992. "The Armani of armor." Exclusive bulletproof fashion apparel.
 - Safariland body ARMOR - since 1964. "Engineered and designed to maximize both ballistic performance and human performance. Every piece in this line has been re-invented and purpose-built for unprecedented protection, comfort and modularity." Body armor has come of age.
 - SafeGuard ARMOR - since 2006. "Protection Personified. Body Armor | Kevlar Body Armor." Affordable Bullet Proof Body Armor From SafeGuard ARMOR, Solutions For Both Military, Security & Civilian Applications, Next Day Delivery Available Worldwide!
 - SafeGuard Clothing - "The Perfect Civilian Body Armor Design." Globally trusted retailer of high quality body armor. All of the protective panels featured in the body armor offered by SafeGuard Clothing consist of 100% DuPont Kevlar.
 - Suitart - Diamond Armor. The most expensive custom tailored suit in the world: CHF2.8 million/US$3.2 million. This individual item is the result of the synergy of luxury, technology and art. Characterized by technical refinements the suit will be custom tailored for the customer. The suit is waterproof due to nano-technological sealing, bulletproof (certified by NATO standards) and equipped with an active cooling system. The lining shows an artwork, which was prominently featured in the Hollywood blockbuster “This Means War”. Additionally, the Diamond Armor is graced with 880 black diamonds decorating the buttons and the lapel.
Computer & Internet Security
 - 2 Online Security Steps You Should Stop Putting Off - The New York Times.
- 4 ways to avoid being a victim of Russian cyberwarfare - "Follow these four simple steps to outflank Putin’s digital foot soldiers."
- 4 Ways to Protect Against the Very Real Threat of Ransomware - Wired.
- 7 Easy Steps to Protecting Your Digital Life - The New York Times.
- 7 Simple Ways to Protect Your Digital Privacy - "You’ve heard about plenty of privacy risks. Here’s what to do next."
- ANTIVIRUS SOFTWARE - Wikipedia.
- Are you secure online? Take the quiz to find out - The Telegraph.
- av comparatives - "Independent Tests of Anti-Virus Software."
- best portable SSD - engadget.
- Behavioural biometrics – the future of security - TechRadar.
- Check if your email has been compromised in a data breach - "Have I Been Pwned allows you to search across multiple data breaches to see if your email address has been compromised."
- CHINESE WALL - definition & explanation.
- COMPUTER SECURITY - Wikipedia.
- CSO SECURITY AND RISK - provides news, analysis and research on a broad range of security and risk management topics.
- DNS Changer Check-Up - check for malware infection.
- Edward Snowden made an app to protect your laptop - The Verge.
- Everyone should cover up their laptop webcams right now - says FBI.
- Fat Finger Syndrome - definition & explanation.
- FIREWALL - definition & explanation.
- Fix DNS Changer infection
- Flaws in Wireless Mice & Keyboards Let Hackers Type on Your PC - Wired.
- Google now has its own hardware security keys - "They're more secure than traditional two-factor authentication methods."
- HIIPAA | Health Insurance Portability and Accountability Act (US) - identifiers, transactions, enforcement, security, privacy, code sets, industry discussion/collaboration, and other resources.
- How Many Times Has Your Personal Information Been Exposed to Hackers? - The New York Times.
- How to protect your PC from the Meltdown & Spectre flaws - The Guardian.
- How to set up two-factor authentication on all your online accounts - The Verge.
- INTERNET SECURITY - Wikipedia.
- MALWARE - Wikipedia.
- Mark Zuckerberg tapes over his webcam. Should you? - The Guardian.
- MOLLUM - web service that helps you identify content quality and, more importantly, helps you stop spam on your blog, social network or community website.
- Monitoring how we use a keyboard and mouse is the next line of security defence - V3.co.uk.
- NAKED SECURITY | COMPUTER SECURITY - "Award-winning news, opinion, advice and research from SOPHOS."
- PCI SECURITY STANDARDS COUNCIL - responsible for the development, management, education, and awareness of the PCI Security Standards, including: the Data Security Standard (DSS), Payment Application Data Security Standard (PA-DSS), and Pin-Entry Device (PED) Requirements.
- THREATPOST - "The First Stop for Security News."
- Top 10 Best Antivirus Providers For Mac (2018) - AntivirusTop10.
- Usability vs. Security - "The Everlasting Trade-Off in the Context of Apple iOS Mobile Hotspots."
- USENIX - The Advanced Computing Systems Association. Since 1975, the USENIX Association has brought together the community of engineers, system administrators, scientists, and technicians working on the cutting edge of the computing world. The USENIX conferences have become the essential meeting grounds for the presentation and discussion of the most advanced information on the developments of all aspects of computing systems.
- WHITE HAT - definition & explanation.
- AVAST! - "Download the new avast! 2014". Over 219 million people rely on AVAST to keep them safe – more than any other security provider. Download avast! 2014 for free now!
- AVG - "FREE 2014 antivirus and anti-spyware security software." For your mobile too.
- AVIRA FREE ANTIVIRUS - "Avira Free Antivirus." Simplicity meets complete online security.
- BULLGUARD - "We keep you safe and we keep it simple."
- Cylance - "Predict. Prevent. Protect." The next generation of advanced threat security. The world's first math and machine learning advanced persistent threat solution for the enterprise.
- ESET - "Wherever you come from, we can protect you." Antivirus software with spyware and malware protection.
- F-SECURE - "Switch On Freedon." F-Secure has been fighting for a safe and secure internet for over 25 years. We build award-winning security solutions to keep you safe at home, in the office, and while on the move. Antivirus software, anti-spyware and Internet security tools.
- FireEye - since 2004. "Cyber Security & Malware Protection." FireEye helps you detect advanced and never-before-seen cyber attacks because it does not rely on signature-based defenses with their barrage of undifferentiated security alerts. By working with FireEye, you can identify connections between alerts, prioritize alerts and get actionable contextual intelligence for rapid remediation.
- G DATA SOFTWARE - "Trust in German Sicherheit." Your life is online. You surf, you shop, you carry out banking transactions and you send emails. Don't leave the protection of your personal data to chance when you do so - rely on G DATA security solutions that meet German quality standards. For over 25 years we have been looking out for you - so you can keep your mind clear for the important things in life. That's German Sicherheit.
- GENIE9 - backup sofware solutions. "Allways have a backup plan!"
- GOOGLE SHARING - how to hide from Google. A special kind of anonymizing proxy service, designed for a very specific threat. It ultimately aims to provide a level of anonymity that will prevent google from tracking your searches, movements, and what websites you visit.
- INTEGO - Mac Antivirus and Security.
 - KASPERSKY LAB - since 1997. "Antivirus Protection & Internet Security Software." International software security group operating in almost 200 countries and territories worldwide. The company is headquartered in Moscow, Russia, with its holding company registered in the United Kingdom. Kaspersky Lab currently employs over 2,850 qualified specialists. It has 31 representative territory offices in 30 countries and its products and technologies provide service for over 300 million users and over 250,000 corporate clients worldwide. The company is specially focused on large enterprises, and small and medium-sized businesses.
- Kroll - "In today’s information economy, data can be your organization’s most valuable asset — but with the rise of mobile technology, cloud computing and an exponentially growing volume of digital information, keeping that data secure also becomes one of your greatest challenges. Kroll is the premier provider of end-to-end cyber security services, with 40 years of experience helping businesses of all sizes face privacy and security issues with evolving, scalable solutions."
- LOGITECH - "Be there even when you're not." Logitech Digital Video Security helps you what matters most even when you can't be there.
 - Lookout - "The best mobile security for individuals and enterprises alike." Lookout gives you a fighting chance of getting your lost or stolen phone back, whether it’s in the couch cushions or lost after a night out.
- MCAFEE - "Safe is not a privilege. It is a right." McAfee is the world’s largest dedicated security technology company. Delivering proactive and proven solutions and services that help secure systems and networks around the world, McAfee protects consumers and businesses of all sizes from the latest malware and emerging online threats. Our solutions are designed to work together, integrating antimalware, antispyware, and antivirus software with security management features that deliver unsurpassed real-time visibility and analytics, reduce risk, ensure compliance, improve Internet security, and help businesses achieve operational efficiencies.
- MICROSOFT MORRO - new anti-malware solution.
- MICROSOFT SECURITY ESSENTIALS - free software helps you avoid viruses, spyware, and other malicious software.
- NORTON - "Stop both today’s and tomorrow’s online threats." Spyware remover and Norton antivirus. Voted #1 computer & Internet security package.
- PREY - "Protect your devices from theft." Prey lets you keep track of your laptop, phone and tablet whenever missing, whether you're in town or abroad. Open source, proven software with hundreds of documented recoveries all around the world.
- SECUNIA PERSONAL SOFTWARE INSPECTOR | PSI - "Free Computer Security." Used by millions of home users around the world, the Secunia PSI is a FREE security tool designed with the sole purpose of helping you secure your computer against vulnerabilities in programs.
 - Silent Circle - since 2012. "The World’s Solution to Mobile Privacy." In a digital world with eyes and ears everywhere, privacy is hard to find. Get in the Circle. Encrypted communications firm providing multiplatform secure communication services for mobile devices, desktop and email.
- SOPHOS - "Cloud antivirus. Complete endpoint, mobile, web, and data security licensed by the user—not the device."
- SPYRECON - "Start secretly recording everything that happens on your computer in minutes with SpyRecon!"
- SYMANTEC - "Do it simply, safely, and quickly. Do it all. Go ahead, you've got Symantec." Endpoint, Cloud, Mobile & Virtual Security Solutions. Antivirus, anti-spyware, endpoint security, backup, storage solutions.
- TREND MICRO - "Global leader in cloud security, Trend Micro develops Internet content security and threat management solutions that make the world safe for businesses and consumers to exchange digital information."
- VERISIGN - "SSL certificates from Symantec Powered by VeriSign."
- YUBICO - "Trust the Net." Secure Login in a simple touch. Two-factor authentication with the YubiKey.
Encryption | Anonymity
 - 7 benefits of using a VPN (spoiler: it could save you money) - "We all regularly use the internet nowadays for a variety of different purposes. Whether it’s to keep in touch with friends and family, to work from home, or to conduct our banking and bill paying online, it’s important to be secure. One of the best ways to keep yourself secure and your activity private is to use a VPN."
- 7 Easy Steps to Protecting Your Digital Life - The New York Times.
- After Paris Attacks, Here’s What the CIA Director Gets Wrong About Encryption - Wired.
- Anonymity application - Wikipedia.
- Apple's statement to Congress on the FBI warrant fight - The Verge.
- Apps to Encrypt Your Smartphone Communications - The New York Times.
- Building a new Tor that can resist next-generation state surveillance - Tor is an imperfect privacy platform. Ars meets the researchers trying to replace it.
- ENCRYPTION - Wikipedia.
- Hashing - transformation of a string of characters into a usually shorter fixed-length value or key that represents the original string.
- how weakened encryption jeopardizes 'secure' sites - The Guardian.
- Is Law Enforcement “Going Dark” Because of Encryption? - The Intercept.
- Meet Moxie Marlinspike, the Anarchist Bringing Encryption to All of Us - Wired.
- Onion routing - Wikipedia.
- ONLINE ANONYMITY - Wikipedia.
- steganography - the practice of concealing a file, message, image, or video within another file, message, image, or video.
- The Father of Online Anonymity Has a Plan to End the Crypto War - Wired.
- Top-Shelf iPhone Hack Now Goes for $1.5 Million - Wired.
- True Private Messaging - 7 Apps to Encrypt Your Chats.
- Trusted third party | TTP - entity which facilitates interactions between two parties who both trust the third party.
- Two Tips to Keep Your Phone’s Encrypted Messages Encrypted - Wired.
- VPN Beginner’s Guide - "What is a VPN and how does it work (Explained)."
- When Phone Encryption Blocks Justice - The New York Times.
- 10 BEST VPN SERVICES 2018 - PCMagazine.
- ANONYMIZER - email & Internet anonymity.
- Crypto AG - since 1952. "High-security products and
services from a single company. End-user, network & radio security: 25 products, 7 systems, 5 services." Swiss company specialising in communications and information security. The company is a long-established manufacturer of encryption machines and a wide variety of cipher devices.
- GOOGLE SHARING - how to hide from Google. A special kind of anonymizing proxy service, designed for a very specific threat. It ultimately aims to provide a level of anonymity that will prevent google from tracking your searches, movements, and what websites you visit.
- Hotspot Shield - since 2005. "Free VPN Service." Allows users to surf the Internet privately by creating a virtual private network so the user can gain secure access to all internet content, while staying in control over their personal privacy.
- HTTPS Everywhere - Firefox and Chrome extension that encrypts your communications with many major websites, making your browsing more secure.
 - I2P - "The Invisible Internet Project." Since 2003. Computer network layer that allows applications to send messages to each other pseudonymously and securely. Uses include anonymous web surfing, chatting, blogging and file transfers. The software that implements this layer is called an I2P router and a computer running I2P is called an I2P node. The software is free and open source and is published under multiple licenses.
- iMessage - instant messenger service developed by Apple Inc. for iOS and OS X Mountain Lion. Not to be confused with Messages (application). iMessage allows users to send texts, documents, photos, videos, contact information, and group messages over Wi-Fi, 3G or LTE to other iOS or OS X users, thus providing an alternative to standard SMS/MMS messaging for all users with devices running iOS 5 or later. On iPhones, green buttons and text bubbles indicate SMS-based communication; on all iOS devices, blue buttons and text bubbles indicate iMessage communication. All iMessages are ENCRYPTED and can be tracked using delivery receipts. If the recipient enables Read Receipts, the sender will be able to see that the recipient has read the message. iMessage also allows users to set up chats with more than two people - a "group chat".
- MEGA - User Controlled Encryption. "Cloud storage will never be the same." Kim Dotcom's new cloud storage service. "The Privacy Company. Bigger. Better. Faster. Stronger. Safer."
- PGP | PRETTY GOOD PRIVACY - data, email & hard drive encryption.
- Proof of Existence - Provides Intellectual Property Rights. Can be used to demonstrate document ownership without revealing the information it contains, and to provide proof that a document was authored at a particular time. The key advantages are anonymity, privacy, and getting a decentralized proof which can't be erased or modified by anyone (third parties or governments).
- PSIPHON - develops a wide range of tools and solutions aimed at preserving security, privacy, and access to content.
- ROBOFORM - password manager and management, form filler, encrypt your passwords, generate random passwords, and more.
 - Secure Drop - open-source whistleblower submission system managed by Freedom of the Press Foundation that media organizations use to securely accept documents from anonymous sources.
 - Silent Circle - since 2012. "The World’s Solution to Mobile Privacy." In a digital world with eyes and ears everywhere, privacy is hard to find. Get in the Circle. Encrypted communications firm providing multiplatform secure communication services for mobile devices, desktop and email.
- Tails - "Privacy for anyone anywhere." Live operating system, that you can start on almost any computer from a DVD, USB stick, or SD card. It aims at preserving your privacy and anonymity, and helps you to: use the Internet anonymously and circumvent censorship; all connections to the Internet are forced to go through the Tor network; leave no trace on the computer you are using unless you ask it explicitly; use state-of-the-art cryptographic tools to encrypt your files, emails and instant messaging.
 - Tor | The Onion Router - system intended to enable online anonymity. Tor client software directs internet traffic through a worldwide volunteer network of servers to conceal a user's location or usage from anyone conducting network surveillance or traffic analysis. Using Tor makes it more difficult to trace Internet activity, including "visits to Web sites, online posts, instant messages and other communication forms", back to the user and is intended to protect users' personal freedom, privacy, and ability to conduct confidential business by keeping their internet activities from being monitored.
- TorGuard - "Online privacy protection services." Anonymous VPN Service: Anonymize and Encrypt all web Traffic through Private VPN Service. Anonymous Proxy: Keep Your Personal Identity Anonymous & Private on Bittorrent. Stealth VPN: Bypass DPI Firewalls and VPN Blocks with TorGuard Stealth VPN. Private Email: Communicate in Complete Security with OpenPGP email Encryption.
- TRUECRYPT - "Free Open-Source On-The-Fly Encryption." TrueCrypt is free open-source disk encryption software for Windows 7/Vista/XP,
Mac OS X and Linux. In case an attacker forces you to reveal the password, TrueCrypt provides and supports two kinds of plausible deniability.
- Wickr - "Top-Secret Messenger. The Internet is Forever. Escape the Internet with Wickr!" Proprietary instant messenger for iOS and Android and of the company that produces it. Wickr allows users to exchange end-to-end encrypted and self-destructing messages, including photos and file attachments.
Password Managers & Generators
 - 1Password will alert you if your password has been leaked - "The database has over 500 million passwords that have been compiled from previous breaches."
- 2 Online Security Steps You Should Stop Putting Off - The New York Times.
- 5 BEST PASSWORD MANAGERS TO SECURE YOUR DIGITAL LIFE - "Keep your logins under lock and key. We picked our favorites for PC, Mac, Android, iPhone, and web browsers."
- A simple regimen for improving your password security - BestVPN.
- An Old Scam With a New Twist - "If you have gotten a message from someone who claims to have dirt on you - and shows off, as proof, a password you’ve previously used - here’s what happened."
- Apple Just Made A Striking New Security Move That Will Impact All Users - "Apple has made a striking password security move that will impact all users, for the better."
- Apps to Manage Passwords So They Are Harder to Crack Than ‘Password’ - The New York Times.
- Best Password Managers for 2020 - "If you use weak passwords (or the same one everywhere) to secure your online accounts, you are only making it easier for someone to compromise your all accounts. Start using one of our top-tested password managers to help you create a unique and strong password for every website." PCMag.
- Best password managers in 2020 - "Free, and paid software to secure your passwords." TechRadar.
- Best Password Managers to Secure Your Digital Life 2020 - "Keep your logins under lock and key. We picked our favorites for PC, Mac, Android, iPhone, and web browser." Wired.
- digital spring clean: how to sort out your passwords, privacy and bulging photo folder - "From those 6,000 cloud-stored selfies to your most guessable and reused passwords, here is an easy, expert guide to wielding a virtual vacuum."
- GET A PASSWORD MANAGER. NO MORE EXCUSES - Wired.
- Google’s new Chrome Extension automatically checks your passwords are still secure - "It’s not the first such service, but it is the free-est."
- Google's New Tool Tells You if Your Password Has Been Hacked - TIME Magazine.
- How to Not Lose Your Data if You Forget Your iPhone Password - Wired.
- How to set up two-factor authentication on all your online accounts - "An extra step of security never hurt anybody."
- How to Share Your Online Accounts the Safe Way - "Be generous, but also be careful."
- How to stay safe online: 15 ways to avoid being hacked - The Telegraph.
- How your passwords can end up for sale on the dark web - "Last month, Zoom joined a long list of companies whose user data has fallen prey to hackers. More than half a million account logins for the hugely popular video conferencing platform were discovered on the dark web, either offered for free or for next to nothing. Here's how your personal info ends up on the dark web -- and what you can do to protect yourself."
- It’s Time To Plan For A Future Beyond Passwords - "Passwords are a problem. They’re hard to remember, they’re easily stolen, they’re published on the dark web and there are too many of them. According to a study by password management company LastPass, the average number of passwords an employee must remember is 191. Nobody can remember that many passwords."
- List of Password managers - Wikipedia.
- Microsoft will no longer let you use '12345' as your password - Mashable.
- Multi-factor authentication - also: two-factor authentication.
- New Resources Available for Password Manager Apps - "Apple has created a new open source project to help developers of password managers collaborate to create strong passwords that are compatible with popular websites. The Password Manager Resources open source project allows you to integrate website-specific requirements used by the iCloud Keychain password manager to generate strong, unique passwords. The project also contains collections of websites known to share a sign-in system, links to websites’ pages where users change passwords, and more."
- Now’s The Perfect Time to Start Using a Password Manager - "Time has no meaning, and we’re all stuck in front of screens. You may as well secure your life while you’re always online."
- One Password to Rule Them All - The New York Times.
- Password - a secret word or string of characters that is used for user authentication to prove identity, or for access approval to gain access to a resource.
- PASSWORD FATIGUE - also known as Password Chaos or more broadly as Identity Chaos.
- Password management - Wikipedia.
- Password manager - Wikipedia.
- Password strength - Wikipedia.
- Password Meter - How Secure is my Password? Free Online Tool - SafetyDetectives.
- Password not accepted: biometric checks the answer? - The Guardian.
- PHONE NUMBERS WERE NEVER MEANT AS ID - Wired.
- Random password generator - Wikipedia.
- RIP passwords: new web standard designed to replace login method - The Guardian.
- Safety first: the short, simple guide to securing all your passwords - "If you log in to every website with the same details, you’re doing it wrong. Here are four easy steps to unhackability."
- Secure Passwords 101 - "Why They Matter + How To Create Them."
- Strong Password Generator - generates new passwords here in your browser, using JavaScript. A strong password: has at least 15 characters; has uppercase letters; has lowercase letters; has numbers; has symbols.
- TAKE THESE 7 STEPS NOW TO REACH PASSWORD PERFECTION - Wired
- THE NEW YUBIKEY WILL HELP KILL THE PASSWORD - Wired.
- The Secret Life of Passwords - The New York Times.
- top 10 most-guessed passwords by hackers - The Telegraph.
- Trump’s Twitter account has extra protections, which could be why it didn’t get hacked - "A lot of high-profile accounts were hit yesterday, but not Trump’s."
- Video Services May Use Artificial Intelligence to Crack Down on Password Sharing - "Still using your ex-roommates cable credentials to watch 'Game of Thrones?'' That may soon be getting a lot harder, thanks to new efforts to crack down on password sharing for pay TV and online video services."
- What Is Password Hashing? - Wired.
- When can we finally get rid of passwords? - "The tech exists to replace them, but adoption is lagging behind."
- Why are so many people using ‘ashley’ as a password? - "It is only the 797th most popular girl’s name in the UK – yet a study shows it is used as a website login more often than any other forename."
- Why Is 3sYqo15hiL Such A Popular Password? - "Improving your password hygiene is one of the most important things you can do to strengthen your security, so why is 3sYqo15hiL such a popular choice?"
- WHY SO MANY PEOPLE MAKE THEIR PASSWORD 'DRAGON' - Wired.
- World Password Day 2016 - "A Password Is Not Enough."
- You need a password manager -- right now - "Don’t reuse that basic password -- you don’t know where it's been."
 - YubiKey NEO - "NFC Security Key." In a single device, the YubiKey NEO has both contact (USB) and contactless (NFC, MIFARE) communications. It supports one-time password, smart card functionality, including OpenPGP and PIV, and the emerging FIDO Alliance Universal 2nd Factor (U2F) protocol. Takes two-factor authentication to the next level. Use it along with a username and password to prove your identity and prevent hackers from breaking into your accounts. It’s specially designed to fit on a keychain, which means it goes wherever they (and their car keys) go." - (Wired.)
- 1Password - since 2006. "The world’s most-loved password manager." 1Password is the easiest way to store and use strong passwords. Log in to sites and fill forms securely with a single click.
- Bitwarden - since 2015. "Open Source Password Management for You and Your Business." The easiest and safest way for individuals and businesses to store, share, and secure sensitive data on any device. We believe that security is important for everyone. The core features of Bitwarden are 100% free.
- Dashlane - since 2009. "The Password Manager, Perfected. Never forget another password." Keep track of all your passwords, whether you use them once a day or once a year. Have them ready when you need them and instantly typed for you.
- Kaspersky Password Manager - since 1989. "Security. Speed. Convenience. All your passwords, documents & data. All in one place. Always to hand." Gives you easy access to your accounts, plus a secure digital vault for your passport, driver’s license, bank cards & other personal data.
- KeePass Password Safe - since 2006. "KeePass is a free open source password manager, which helps you to manage your passwords in a secure way. You can put all your passwords in one database, which is locked with one master key or a key file. So you only have to remember one single master password or select the key file to unlock the whole database. The databases are encrypted using the best and most secure encryption algorithms currently known (AES and Twofish)."
- Keeper - since 2008. "Cybersecurity starts with password security." Keeper is the top-rated password manager for protecting you, your family and your business from password-related data breaches and cyberthreats.
- Last Pass - since 2008. "Simplify your online life." LastPass remembers all your passwords across every device for free! Auto-pilot for all your passwords.
- LogMeOnce - "PasswordLess & Smarter Identity Management." Since 1995 we have invented award-winning security products. 100% Improve your password security and achieve “A+” grade. Whether you have an average password grade or even an “F,” LogMeOnce will quickly help you improve your password security. LogMeOnce Dashboard provides tips and prioritizes which passwords to fix first. See the three weakest passwords and why they’re scoring so poorly. As soon as you make improvements, watch your score go up. Achieve progress with the help of LogMeOnce’s automated self-service - before you know it, you’ll achieve an A+.
- mSecure - since 2008. "Don’t sacrifice your security for convenience." mSecure is the most secure and straightforward solution to storing, sharing, and managing passwords and sensitive information. Secure your data and passwords behind industry standard AES-256 encryption.
- NordPass - since 2008. "Autosave & Autofill Passwords. We lock passwords. You hold the key." With NordPass, store your passwords in the cloud, access them on desktop, mobile, or your favorite browser. All encrypted on your device, for your eyes only. Manage your passwords effortlessly. Never reset passwords again. Access them whenever you need them, on any device.
- Norton Password Generator - Norton Password Manager - since 1990. "Create Safe & Secure Passwords." Create strong passwords with Password Generator ... Use the slider, and select from the options, below, to lengthen your password and strengthen your security.
- RoboForm - since 2000. "Protect Your Passwords." You’ll never need to remember or type your passwords again. One click convenience. RoboForm securely stores all of your passwords and logs you in with a single click (or tap). Save time entering personal and billing information with AutoFill for long web forms.
- Trend Micro Direct Pass - since 1988. "Free Password Manager Software." Simple, secure password management. Manage up to 5 passwords. No expiration.
- True Key by McAfee - since 1987. "Sign in to True Key and we'll log you in everywhere else." Sign in to True Key and we'll log you in everywhere else. Password management is automatic. True Key auto-saves and enters your passwords, so you don't have to.
- Zoho Vault - since 1996. "Password Manager for Teams, Businesses, Enterprises. Say goodbye to remembering passwords." Let us do it for you. Manage passwords, and securely autofill them across websites and applications using Zoho Vault. Get clear security insights into both your personal and business passwords. Identify any weak passwords and change them in just a few clicks.
Safe Boxes
 - DAS SAFE - since 1984. "Anonymous & Non-Anonymous Safes & Data Storage. "There are always things, that you shouldn't have at home". Rent safes per week, per month, or per year. Guaranteed security: 1000 tons of reinforced concrete surround the vault which is protected by a perfect electronic system. In addition the building is guarded day and night. DAS SAFE in Palais Auersperg is located close to the parliament, on Auerspergstrasse 1, at the corner of Lerchenfelder Strasse in 1080 Vienna, Austria.
 - Le Freeport - "A high-end, ultra safe facility for the storage of valuable goods." LE FREEPORT sets new standards, demanded by investors and collectors alike: a purpose built facility combining cutting edge technology, efficient logistics, and an exhaustive range of expert services. LE FREEPORT is the ideal platform for securing, servicing and selling works of art and other valuables. Luxembourg & Singapore.
- SAFE - Wikipedia.
- SAFE DEPOSIT BOX - Wikipedia.
- Über-warehouses for the ultra-rich - "Ever more wealth is being parked in fancy storage facilities. For some customers, they are an attractive new breed of tax haven."
 - Agresti - Firenze 1949. All models.
 - boca do lobo - "Luxury Safes."
 - Brown Safe Manufacturing - since 1980. "The world’s premiere safe and vault company providing high security solutions around the globe."
- BUBEN & ZÖRWEG - since 1995. Luxury safes.
 - Casoro Jewelry Safes - "Custom Luxury Jewelry Safes." Unique designer styling with maximum security. Variety of customizable features and security options.
- CHUBBSAFES - founded in 1818. "Trusted the world over."
 - DÖttling - "Around the world, Döttling safes find homes among select connoisseurs and enthusiasts of the finest locksmith artisanry since 1919."
- ELECTRONIC SAFE MANUFACTURERS & SUPPLIERS
- FIRST SECURITY SAFE CO.
- GARDEX - burglary and fire resistant safes and filing cabinets.
- John Tann - "Our Products and service covers the range of technical equipping of safes, vault doors, and strong rooms, day and night safes, deposit boxes, and maintenance."
- Mosler Safe Company - (1867-2001).
- Rosengrens - since 1847. "We stand by you." Brand of safes and vaults with its origins in Sweden. It specialises in products which offer certified burglary protection and/or fire protection.
- SAFE SECURITY SERVICES LTD.
- SECRET STORAGE BOOKS - home-based craft business which hand makes hidden storage boxes from old books.
- SENTRY SAFE - uses extremely rigorous, UL and ETL testing standards to ensure that your irreplaceables are protected from fire, water and theft.
 - STOCKINGER - "Safety First Class." Bespoke and handcrafted in Germany since 1978.
 - Stockinger for Bentley - Wikipedia.
- Sun Welding Safe Company - "Hand Crafted in the USA Since 1980."
 - UNDERWOOD LONDON - "The safest way to protect your watches both automatic and non-automatic and all of your jewellery items as well."
Security Resources
 - 4GB SPY VIDEO CAMERA WATCH W / HIDDEN CAMERA V2 - from BUDGETGADGETS.COM.
- 8GB DIGITAL SPY PEN - image capture, video recording (VOX).
- AK-47 | Avtomat Kalashnikova - is a selective fire, gas operated 7.62mm assault rifle. The original AK-47 and its numerous variants are the most widely used and popular assault rifles in the world. KALISHNIKOV HOMEPAGE - dedicated to Kalashnikov and his firearms.
- Anti-surveillance gadgets for protesters - Ars Technica.
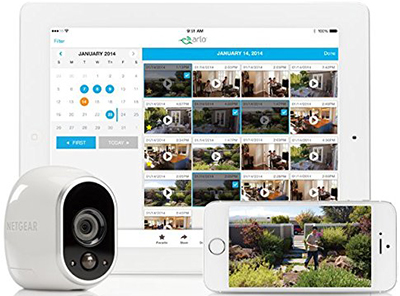 - Arlo - "The world's first 100 percent wireless high-definition smart home security camera."
 - Armatix - 'Smart' Firearms.
- ARMOR GROUP - the world's leading security solutions group.
- ARMORCO - "Your protection is our priority." Distributor / manufacturer of hi-tech bullet resistant materials and personal protection products.
- ARMY TECHNOLOGY - the website for the defence industries - army.
- ASSA ABLOY - the global leader in door opening solutions.
- AUDI SECURITY CARS - "You are in an especially safe place when you’re in an Audi Security car".
 - AXON Flex - "A New Generation of Police Video Camera." The AXON Flex is a point-of-view video camera system designed to be worn by law enforcement officers to capture video and audio from their perspective. There also is an app that allows for the live viewing or immediate playback on a smart phone of what the camera captures. The unit is activated simply by pressing the large button on the power pack, which is attached to the camera via a small wire.
- BAE SYSTEMS - global company engaged in the development, delivery and support of advanced defence, security and aerospace systems in the air.
- BALLISTIC STANDARDS - independent product verification and qualification testing.
- Beau Dietl & Associates - since 1985. New York private investigators specializing in background checks, asset recovery and security.
- Belgian Malinois dog - U.S. Secret Service uses Belgian Malinois to guard the grounds of the White House.
- best portable SSD - engadget.
- Beware the smart toaster: 18 tips for surviving the surveillance age - The Guardian.
 - Blackphone - secure voice, video, conferencing, file transfer, and text communications.
- BLACKWATER WORLDWIDE - a private military security company founded in 1997. Has now changed its name to Xe Services LLC.
 - Boing Black Smartphone - "Security, modularity and productivity delivered – all in one trusted mobile device." The Boeing Black has a dual-SIM capability that allows users to switch between government and commercial networks, and works globally on GSM, WCDMA, and LTE bands. Boeing said the smartphone's 5.2-inch-tall shell can be customized with additional sensors, an extra battery, satellite transceivers, biometrics, and other hardware.
- BOOK VAULT - two random hardcovers hollowed out to hold stuff.
- BOSCH - "Invented for life."
- BOTACH TACTICAL - "Your Professional Specialist Serving Those Protecting Our Great Country."
- CAMPCO - watches, law enforcement equipment, handcuffs, pepper spray, stun guns.
 - Canary Security Device - "A complete security system in a single device." Smarter home security starts here. Stay in the know on everything that goes on in your home, even when you're not there. Canary keeps you connected to the people and places that matter most.
- CARBON MOTOS CORPORATION - police car E7.
- CARDOK - your own undergorund parking space. Security to protect your car(s).
- CASTLE SHIPBOARD SECURITY PROGRAM - provides advanced training in shipboard security and vessel defense. The yacht charter industry is one of our primary client categories.
- CCS | COVERT CAMERA SOLUTIONS
- CENTIGON - security vehicles, armored cars, special limousines. World's largest armored vehicle manufacturer and global security systems provider.
- CHINAVASION - security equipment from China.
- CHINAVASION - surveillance equipment from China.
- COMPRO TECHNOLOGY - IP cameras, home surveillance.
- COPS PLUS - the source for police supplies, duty gear and tactical police equipment.
- CREDIT CARD LOCK PICK - it contains 4 of the finest stainless steel picks ever made, and a double-ended tension tool of .035 spring stainless steel. There are 3 cavities in the base of the credit card that hold 2 pairs of picks with the tension tool in the middle. The card set is less than 1/8 inch thick and fits into the same space as a credit card! The Ultimate Spy Gadget!
- Croma Security SOLUTIONS - "Protecting the things that matter." At Croma we go further to secure the things that matter to you. Whether you need to protect your home, business, people or assets, we are there as your trusted security partner – providing award-winning systems and solutions that deliver the peace of mind and protection you need.
- CROSSMATCH TECHNOLOGIES - global provider of best-in-class, multimodal biometric identity management solutions.
 - Crypto AG - since 1952. "High-security products and
services from a single company. End-user, network & radio security: 25 products, 7 systems, 5 services." Swiss company specialising in communications and information security. The company is a long-established manufacturer of encryption machines and a wide variety of cipher devices.
- CRYPTO MUSEUM - "At present we are a virtual museum in The Netherlands, that can only be visited on the internet. We do, however, regularly organize exhibitions in co-operation with other museums."
 - Cyborg Unplug - "Your defense against wireless surveillance." Anti wireless-surveillance system for the home and workplace. It detects and kicks selected devices known to pose a risk to personal privacy from your wireless network, breaking uploads and streams.
Cyborg Unplug hits wireless surveillance devices where it hurts: network connectivity. 'Plug to unplug', it sniffs the air for wireless signatures from devices you don't want around, sending an alert to your phone when detected. Should the target device connect to a network you've chosen to defend, Cyborg Unplug will immediately disconnect them, stopping them from streaming video, audio and data to the Internet.
 - DAMILIC - "The World Leader in Handwriting Automation." Automatic signing machines: Autopen, Signacript and Signature Systems (simulated handwriting software). Read also: Obama's signature: Is it real or is it autopenned?.
- DAS SAFE - since 1984. "Anonymous & Non-Anonymous Safes & Data Storage. "There are always things, that you shouldn't have at home". Rent safes per week, per month, or per year. Guaranteed security: 1000 tons of reinforced concrete surround the vault which is protected by a perfect electronic system. In addition the building is guarded day and night. DAS SAFE in Palais Auersperg is located close to the parliament, on Auerspergstrasse 1, at the corner of Lerchenfelder Strasse in 1080 Vienna, Austria.
- DAZZLER (WEAPON) - Wikipedia.
- Default Tech Settings You Should Turn Off Right Away - "These controls, which are buried inside products from Apple, Google, Meta and others, make us share more data than we need to."
- Defence Security and Equipment International | DSEI - since 1999. "The World Leading Defence & Security Event." Defence and security equipment exhibition held every two years in London Docklands, which draws thousands of visitors, both trade and military. It is the world’s largest fully integrated international defence exhibition featuring land, sea and air products and technologies.
- DIRECTORY OF SUPPLIERS OF SURVEILLANCE EQUIPMENT
- DPL SURVEILLANCE EQUIPMENT
- DROPBOX - the easiest way to store, sync, and, share files online. free download.
 - Dropcam Pro WiFi Video Monitoring with Cloud Recording. Setup in Minutes

- ELBIT SYSTEMS - a global defense electronics company.
- Eurosatory - International Defence & Security industry trade show that is held every two years in Paris-Nord Villepinte Exhibition Centre, Paris, France.
- Eye Tap - device that is worn in front of the eye that acts as a camera to record the scene available to the eye as well as a display to superimpose a computer-generated imagery on the original scene available to the eye.
- FAKE NAME GENERATOR - "Generate a Random Name." The most advanced name generator. With 30 languages and 22 countries, the Fake Name Generator is the most advanced name generator on the internet.
- Fastvein - "Beyond the fingerprint." The most advanced biometric system in the world providing the equivalent security & accuracy of iris scanning, but at a fraction of the cost.
- FireEye - since 2004. "Cyber Security & Malware Protection." FireEye helps you detect advanced and never-before-seen cyber attacks because it does not rely on signature-based defenses with their barrage of undifferentiated security alerts. By working with FireEye, you can identify connections between alerts, prioritize alerts and get actionable contextual intelligence for rapid remediation.
- Foiling Cyberspies on Business Trips - The New York Times.
- Forensics For Dummies Cheat Sheet - For Dummies.
- FRANK M. AHEARN - "The leader in teaching people how to disappear. For over twenty years Frank M. Ahearn has been considered one of the leading skip tracers in the world."
- FRAUD-PROOF CREDIT CARD POSSIBLE BECAUSE OF QUANTUM PHYSICS - University of Twente, Enschede, Netherlands.
 - Gate - "The First Camera-Equipped Smart Lock." Gate enhances your deadbolt with a motion-activated camera, keypad, and 2-way audio. Manage everything from your phone.
- General Data Protection Regulation (GDPR) - EU Parliament.
- GENERAL DYNAMICS SECTÉRA EDGE SMARTPHONE - Secure Mobile Environment Portable Electronic Device (SME PED).
- GF PROTECTION - intelligence & safety.
- GILARDONI - X-ray and ultrasonic solutions for security, medical diagnostics, non-destructive testing (NDT) and OEM components.
- GLARE MOUT - non-lethal visual disruption laser by B.E. Meyers Electro Optics.
- GOOGLE SHARING - how to hide from Google. A special kind of anonymizing proxy service, designed for a very specific threat. It ultimately aims to provide a level of anonymity that will prevent google from tracking your searches, movements, and what websites you visit.
- Guide: Extreme online security measures to protect your digital privacy - The Guardian.
 - Hacking Team - "Here in HackingTeam we believe that fighting crime should be easy: we provide effective, easy-to-use offensive technology to the worldwide law enforcement and intelligence communities. Technology must empower, not hinder. Exclusively focused on offensive security, HackingTeam was founded in 2003. In 2004, we were the first to propose an offensive solution for cyber investigations, with such a strong reception that in 2007 we were venture backed. All the development is made in Milan, by a team of 50+ professionals focusing on all the aspects of offensive security, Our technology is used daily to fight crime in six continents."
- HART SECURITY - land, sea & air security.
- HIDDEN CAM - videos, equipment, & reviews.
- HIDDEN SPY COMPANY - spy cameras.
- How Many Times Has Your Personal Information Been Exposed to Hackers? - "There’s been another mega-breach. Marriott said Friday that information for as many as 500 million of its customers may have been stolen. Answer the questions below to learn which parts of your identity may have been stolen in the last five years. Not all attacks are included here, and many attacks go undetected, so think of your results as a minimum level of exposure."
- how smart devices are outsmarting criminals - The Guardian.
- How Spy Tech Firms Let Governments See Everything on a Smartphone - The New York Times.
- How to avoid being kidnapped abroad (by someone who was) - The Telegraph.
- How to stay safe online: 15 ways to avoid being hacked - The Telegraph.
- How to Survive Airport Security - The New York Times.
- IMS SECURITY - offers Israeli style security services and tactical training. Specializing in protecting Hollywood actors and providing tactical training.
- IMSI catcher - an IMSI catcher (International Mobile Subscriber Identity) is a telephony eavesdropping device used for intercepting mobile phone traffic and tracking movement of mobile phone users.
- INTERNATIONAL ARMORED GROUP - custom armored vehicle builder.
- INSSIDER - an award-winning FREE WI-FI NETWORK SCANNER for Windows Vista and Windows XP.
- INTELIUS - "Live in the know." Pioneers in the information commerce industry, innovating technologies to collect, interpret and deliver information to consumers and businesses online. Advanced people search in the U.S. Background check. Reverse cell phone lookup.
- INTERNATIONAL SECURITY ACADEMY - "Our programs include 4 focal areas: 1. Close Protection, 2. High Risk Protection, 3. Maritime Protection, 4. Protection & Counter Terrorism Instructors. The International Security Academy's' activities are recognized, authorized and supervised by the State of Israel and other countries where our practical training centers are activated."
- International Spy Museum - since 2002. Washington, DC, U.S.A. The Museum features the largest collection of international espionage artifacts ever placed on public display. It is the only public museum in the United States solely dedicated to espionage and the only one in the world to provide a global perspective on an all-but-invisible profession that has shaped history and continues to have a significant impact on world events.
 - IOSAFE - "Disaster proof hardware." Go-Anywhere ioSafe Rugged Portable Hard Drive.
- IRONKEY - the world's most secure flash drive.
- J.A. HARKINS CUSTOM KNIVES
- JANE'S INFORMATION SOLUTIONS - intelligence and insight you can trust.
- JIANGSU ANHUA POLICE EQUIPMENT MANUFACTURING CO. - anti-riot suits, handcuffs, police batons, traffic, extendible, retractile and electric batons, bulletproof vests, road blocker, fetters, body armor, duty leather/security belt, Normex masks, metal detectors, traffic baton, tactical goggles.
- KABA ILCO - a worldwide leader and innovator in providing electronic hotel lock solutions. Key systems. Access control.
- KGB CAMERAS - wireles and CCTV video cameras.
- Krebs on Security - "In-depth security news and investigation."
- Kroll - corporate investigations and risk consulting firm based in Midtown Manhattan, New York City. It was established in 1972. It is the world's leading risk and security consultancy.
-
- LAS VEGAS RESORT USING MICROWAVES TO KEEP GUNS OUT OF ITS CASINO - Wired.
- LASER DAZZLER - LE Systems Inc.
- LIFEGUARD - "Be Smart. Be Safe. Get LifeGuard Personal Breathalyzer." The LifeGuard breath alcohol tester is a high quality device to help you manage your Blood Alcohol Content (BAC). The LifeGuard breathalyzer uses the same fuel cell technology as Law Enforcement instruments, giving you the most accurate BAC readings to help you manage your BAC.
- LIST OF HANDCUFFS MANUFACTURERS
 - Lookout - "The best mobile security for individuals and enterprises alike." Lookout gives you a fighting chance of getting your lost or stolen phone back, whether it’s in the couch cushions or lost after a night out.
- LOOMIS - managing cash in society.
- LORRAINE ELECTRONICS - manufacturer and distributor of covert electronic surveillance equipment.
- LWRC INTERNATIONAL - reliable tools for the warfighter, law enforcement professional and civilian shooter.
- Man watches from his phone as robbers break into his apartment - New York Post.
- Mastering Bitcoin: Unlocking Digital Cryptocurrencies
 - essential reading for everyone interested in learning about bitcoin basics, the technical operation of bitcoin, or if you're building the next great bitcoin killer app or business. From using a bitcoin wallet to buy a cup of coffee, to running a bitcoin marketplace with hundreds of thousands of transactions. - essential reading for everyone interested in learning about bitcoin basics, the technical operation of bitcoin, or if you're building the next great bitcoin killer app or business. From using a bitcoin wallet to buy a cup of coffee, to running a bitcoin marketplace with hundreds of thousands of transactions.
- MICRO SURVEILLANCE EQUIPMENT
- Milipol - since 1984. "Worldwide exhibition of internal State security." The world’s leading security exhibition.
- MINOX DSC DIGITAL SPYCAM - "License to Shoot." Seeing this camera makes people immediately think of Bond, James Bond, and not without good reason. The DSC is small, really small. It’s so tiny it disappears in a clenched fist. Just 86 × 29 × 20 mm. 5.1 megapixel CMOS Sensor.
- MyOneSpy - "Cell Phone Spy Software to Track & Monitor Mobile Phones & Tablets." Offering an undetectable cell phone spy software to track and monitor any Android, Blackberry, iPhone and tablet.
 - Nest Protect - "We made a smoke and CO alarm you’ll love, because hating it is dangerous."
 - Netatmo Presence - "Outdoor Security Camera with People, Car and Animal Detection." Prevent break-ins or damage on your property. Ultra-precise alerts let you know instantly about what happens outside your home. Use live stream to view your property in real-time. At night, either watch discreetly with Presence's infra-red night vision or switch the camera's floodlight on. The smart floodlight can be switched on manually in the app or set to switch on when it detects a person, car or animal - or for all three. It helps you find your way safely at night and deters any unwanted visitors.
 - Netatmo Welcome - "Home Security Camera with Face Recognition." Sends the names of the people it sees directly to your smartphone. Be notified when your children or elderly parents are home. The security camera also alerts you when it sees a stranger.
 - Nimb - "Smart Ring That Helps You Feel Safe & Sound." The ring with a panic button to send an alert to friends & family, emergency services, community members & people nearby.
- Online tracking - A 1-million-site measurement and analysis Draft: July 11th, 2016. Princeton University.
- ONPOINT TACTICAL - "Legendary Skills for Today's Professionals." Offers superior training for military, law enforcement, and select professionals & civilians who require advanced outdoor skills.
- OPTOELECTRONICS - manufactures and distributes test equipment, receivers, and frequency counters for use in the scanning hobby, commercial radio, and law enforcement.
- OPTOSECURITY - OptoSreener: designed as a first-line detection system aimed at preventing terrorist events or attacks that may occur in high-profile and critical facilities (e.g. airports).
 - Osdin Shield - "Protection Furiture." We design, create and build, unique, bespoke, ballistic resistant furniture.
- OVERPLAY - "By rerouting your internet connection through our worldwide VPN servers you can: change your IP address to one in another country; improve your security by ensuring your internet traffic is encrypted; access content that is normally restricted at your location."
- Pacsafe - "Smart Travel Gear." Anti-Theft Travel Bags and Travel Accessories.
- PEOPLE SEARCH PRO - free people search, search people, phone numbers, or public records for free.
- PEOPLE SMART - people search & background checks by name, phone, email or address. Find contact information, social networking data, and public records in a way that respects privacy.
 - Piper - "Smart, elegant security and home automation." Home security and automation device with HD camera, environmental sensors, and Z-Wave home automation abilities.
- PLASTIC HANDCUFFS
 - POLY-CONTROL - "Bulding and Home Control." Specialists when it comes to wireless solutions for your buildings or private homes. The solutions are 100% wireless, installed easily by you. The products are sold through resellers all over the world.
- PRIVACY INTERNATIONAL - founded 1990. Surveillance and privacy watchdog.
- Privacy phone wars: Boeing Black vs. the Blackphone vs. Snowden Phone - SiliconANGLE.
- Proof of Existence - Provides Intellectual Property Rights. Can be used to demonstrate document ownership without revealing the information it contains, and to provide proof that a document was authored at a particular time. The key advantages are anonymity, privacy, and getting a decentralized proof which can't be erased or modified by anyone (third parties or governments).
- PSIPHON - web proxy designed to help Internet users securely bypass the content-filtering systems used to censor the internet by governments in places like China, North Korea, Iran, Syria, Myanmar, Saudi Arabia, and others.
- ROBERT WITTMAN INC. - security, protection and recovery of your art investments.
- Russian face recognition company that could end public anonymity is going global - Fusion.
- SANYO CCTC SYSTEM - CCTC security systems.
- SAVELEC - aims to provide a solution for the external, safe control of a non cooperative vehicle without any consequences on the persons inside the vehicle or other persons and objects nearby.
- SECOND CHANCE ARMOR - the first one to use kevlar for body armor.
- Secure Mobile Apps - The Guardian Project.
- SECURESAFE PRO - password and credit card manager software.
- SECURITY CAMERAS DIRECT
- SECURITY MAGAZINE - solutions for enterprise security leaders.
 - Selecta DNA - "Advanced Forensic Marking." Reduces burglaries by up to 83%. By using SelectaDNA to mark your property with a unique DNA identifier, we can help you protect your home or business, so that you don’t become a victim too. Protecting your home with SelectaDNA makes you less likely to be burgled. In fact, 93% of UK Police Forces have used SelectaDNA to bring down crime.
 - Shonin Streamcam Wearable Camera - "Capture YOUR side of the story." Simplifies personal security. It'll broadcast directly to Facebook Live & YouTube.
- SMARTPHONE SECURITY 101: THE STEPS THAT MATTER MOST - Wired.
- SMITH & WARREN - "Custom Badges manufactored in 3 weeks!".
- SMITH & WESSON - since 1852. Firearms, knives, handcuffs, accessories, and more.
- Snowden Designs a Device to Warn if Your iPhone’s Radios Are Snitching - Wired.
- sousveillance - definition & explanation.
 - SpiderOak - since 2007. "Store. Sync. Share. Privately." SpiderOak makes it possible for you to privately store, sync, share & access your data from everywhere. US-based online backup tool to back up, share, sync, access and store data using an off-site server. The software uses encrypted cloud storage and client-side encryption key creation, so even employees of SpiderOak cannot access users' information. In a July 2014 interview, former NSA contractor Edward Snowden recommended SpiderOak over Dropbox, citing its better protection against government surveillance.
- SPY GADGET WAREHOUSE - "Satisfy Your Inner Spy."
- SPYMODEX - cell phone jammer, detectors, and other gadgets.
- STOOF INTERNATIONAL - international manufacturer of armoured and specialty vehicles. Offers after-sales support and security driver training. Based in Germany.
- STUN GUN
 - TASER - "The Safest, Most Effective Options for Personal Protection for You and Your Family."
  - Terrapin Technology - "The Terrapin Technology Briefcase in cognac is made from genuine Italian leather. It contains Honeywell Spectra Shield within the back face and the flap, giving an excellent surface area of protection from 9mm bullets, knives and shrapnel."
- THE STRONGBOX PASSWORD SECURITY SYSTEM - website security: cryptographically secure site defense system.
- Top Secret Museum - Oberhausen, Germany. "The World's Most Comprehensive Exhibit On Espionage."
- TRAVEL RISK MAP 2016 - Global health & travel security risks review.
- TWO WAY MIRROR - custom cut to the size you need.
- Tychem - "Protecting Industrial Workers for 30 Years." Not all deadly threats come in the form of guns or other weapons. For protection against chemical dangers, industrial workers rely on DuPont Tychem garments.
- UNDERGROUND VAULTS & STORAGE - specializes in secure records and asset storage and management. UV&S serves national and international clients representing numerous industries including healthcare, legal, financial, insurance, cultural, oil/gas, entertainment, and government.
- UNIVERSAL HANDCUFF KEY - plastic handcuff key. Undetectable by metal detectors. Opens all cuffs.
- U.S. TRAINING CENTER - training today to meet the challenges tomorrow.
- UZI - the official UZI website.
- VERISIGN - SSL certificates, and more.
- VIP BODY ARMOR - "The premier provider in bulletproof fashion, VIP Body Armor / VIP Body Armor designs bulletproof clothing that embodies fashion with security."
- WISEKEY - founded in 1999. Provides specialized security and digital identification cutting edge technologies for personal data protection, effective identification and authentication of people and objects.
 - Withings Home - "Security is a beautiful thing." Be home from anywhere. With its ability to stream HD video and facilitate family interactions, the Withings Home is the most comprehensive house monitoring solution. Home works with your smartphone, your tablet, your Apple watch and is the first camera you can stream on your Apple TV.
- XE SERVICES LLC - "Where excellence is the standard." Still usually referred to as "Blackwater", is a private military security company founded as Blackwater USA in 1997.
- You Should Stop Using Texts for Two-Factor Authentication - Wired.
- Your battery status is being used to track you online - The Guardian.
 - YubiKey NEO - "NFC Security Key." In a single device, the YubiKey NEO has both contact (USB) and contactless (NFC, MIFARE) communications. It supports one-time password, smart card functionality, including OpenPGP and PIV, and the emerging FIDO Alliance Universal 2nd Factor (U2F) protocol. Takes two-factor authentication to the next level. Use it along with a username and password to prove your identity and prevent hackers from breaking into your accounts. It’s specially designed to fit on a keychain, which means it goes wherever they (and their car keys) go." - (Wired.)
|
|













































































